主题
-
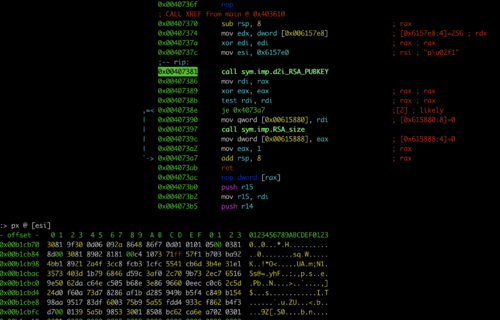
获取当前机器的明文密码在导出域hash之前,我们可以先尝试导出当前机器的本地的hash密码,如果域用户之前在这台机器上进行登陆操作的话,可以直接获取到域用户甚至域管理员的账号。 在Windows操作系统上,sam数据库(C:\Windows\System32\config\sam)里保存着本地用户的hash。 在本地认证的流程中,作为本地安全权限服务进程lsass.exe也会把用户密码缓存在内存中(dmp文件)。 因此,在这里我们可以考虑两种方式进行抓取当前机器的hash:在线工具提取,离线分析提取。 注意:在windows 10\ 2012r2之后的系统版本中,默认情况下已禁用在内存缓存中存系统用户明文密码,此时再直接使用mimikatz去抓明文,肯定是抓不到的。密码字段位会直接显示为null。 这里我们手动修改注册表让其保存明文,方便我们进行抓取。(修改后需要注销用户再登陆) reg add HKLM\\SYSTEM\\CurrentControlSet\\Control\\SecurityProviders\\WDigest /v UseLogonCredential /t REG\_DWORD /d 1 /f mimikatzmimikatz是法国人benjamin开发的一款功能强大的轻量级调试工具,本意是用来个人测试,但由于其功能强大,能够直接读取WindowsXP-2012等操作系统的明文密码而闻名于渗透测试,可以说是渗透必备工具。 下载地址:https://github.com/gentilkiwi/mimikatz 1.通…
-
Ubuntu: USN-7263-1 (CVE-2025-1009): Firefox vulnerabilities Severity 4 CVSS (AV:L/AC:M/Au:N/C:P/I:P/A:P) Published 02/04/2025 Created 02/13/2025 Added 02/12/2025 Modified 02/12/2025 Description An attacker could have caused a use-after-free via crafted XSLT data, leading to a potentially exploitable crash. This vulnerability affects Firefox < 135, Firefox ESR < 115.20, Firefox ESR < 128.7, Thunderbird < 128.7, and Thunderbird < 135. Solution(s) ubuntu-upgrade-firefox References https://attackerkb.com/topics/cve-2025-1009 CVE - 2025-1009 USN-7263-1
-
Debian: CVE-2024-36933: linux -- security update Severity 4 CVSS (AV:L/AC:M/Au:N/C:P/I:P/A:P) Published 05/30/2024 Created 06/04/2024 Added 06/04/2024 Modified 07/03/2024 Description In the Linux kernel, the following vulnerability has been resolved: nsh: Restore skb->{protocol,data,mac_header} for outer header in nsh_gso_segment(). syzbot triggered various splats (see [0] and links) by a crafted GSO packet of VIRTIO_NET_HDR_GSO_UDP layering the following protocols: ETH_P_8021AD + ETH_P_NSH + ETH_P_IPV6 + IPPROTO_UDP NSH can encapsulate IPv4, IPv6, Ethernet, NSH, and MPLS.As the inner protocol can be Ethernet, NSH GSO handler, nsh_gso_segme…
-
Ubuntu: USN-6067-1 (CVE-2022-3277): OpenStack Neutron vulnerabilities Severity 7 CVSS (AV:N/AC:L/Au:S/C:N/I:N/A:C) Published 03/06/2023 Created 05/11/2023 Added 05/11/2023 Modified 01/30/2025 Description An uncontrolled resource consumption flaw was found in openstack-neutron. This flaw allows a remote authenticated user to query a list of security groups for an invalid project. This issue creates resources that are unconstrained by the user's quota. If a malicious user were to submit a significant number of requests, this could lead to a denial of service. Solution(s) ubuntu-upgrade-python-neutron ubuntu-upgrade-python3-neutron …
-
Microsoft Windows: CVE-2023-24906: Microsoft PostScript and PCL6 Class Printer Driver Information Disclosure Vulnerability Severity 7 CVSS (AV:N/AC:L/Au:S/C:C/I:N/A:N) Published 03/14/2023 Created 03/15/2023 Added 03/14/2023 Modified 01/28/2025 Description Microsoft PostScript and PCL6 Class Printer Driver Information Disclosure Vulnerability Solution(s) microsoft-windows-windows_10-1507-kb5023713 microsoft-windows-windows_10-1607-kb5023697 microsoft-windows-windows_10-1809-kb5023702 microsoft-windows-windows_10-20h2-kb5023696 microsoft-windows-windows_10-21h2-kb5023696 microsoft-windows-windows_10-22h2-kb5023696 microsoft-windows-w…
-
Red Hat: CVE-2024-38600: kernel: ALSA: Fix deadlocks with kctl removals at disconnection (Multiple Advisories) Severity 4 CVSS (AV:L/AC:L/Au:M/C:N/I:N/A:C) Published 06/19/2024 Created 12/06/2024 Added 12/05/2024 Modified 12/05/2024 Description In the Linux kernel, the following vulnerability has been resolved: ALSA: Fix deadlocks with kctl removals at disconnection In snd_card_disconnect(), we set card->shutdown flag at the beginning, call callbacks and do sync for card->power_ref_sleep waiters at the end.The callback may delete a kctl element, and this can lead to a deadlock when the device was in the suspended state.Namely: * A process…
-
将对应 gcc.exe 和 go.exe 的路径替换成你自己的,然后重启主程序就可以使用了。 从20231208版本以后,你可以自己选择c编译器:tdm-gcc或者tcc。tcc生成的体积更小(实测7kb,使用upx可以压到5kb以内),但是不支持自定义程序图标。 生成路径中不要包含中文和空格,否则会生成失败! 针对Cobalt Strike,不要选择生成Windows分阶段木马、Windows无阶段木马,而是生成payload,最终是一个payload.c文件。 下载之后本地打开:(记得关闭杀软) 2. 环境配置 安装环境:Windows10虚拟机 在这里新版本掩日采用了gcc环境和go环境,在作者的项目介绍中,对其都有要求,我们按照要求分别安装gcc和go的环境: gcc安装 gcc --version go安装 go version 3. 环境 在作者的介绍中,针对Cobalt Strike生成的木马要求: 针对Cobalt Strike,不要选择生成Windows分阶段木马、Windows无阶段木马,而是生成payload,最终是一个payload.c文件。 因此在这里我们使用最常用的CS的木马来进行操作。 3.1 环境准备 在本地启动一个CS,服务端: sudo ./teamserver 10.30.1.147 123 启用客户端,并新增监听,在这里使用作者建议的HTTPS方式: 然后生成一个payload.c文件: 3.2 测试环境 测试机: Windows10 360主动防御 Windows7 火绒主动防御 W…
-
这次的目标是个购物站点,希望发现更多的漏洞,最好是能拿到shell。 一些常见的漏洞都存在,比如任意修改他人密码、修改商品金额等逻辑漏洞都是存在的。但这里就不提这些逻辑漏洞了,这里说一说ssrf。 注册会员后,前台很多上传点,但是均无法上传shell。 通过nmap扫描端口发现对外开放了3306端口,也就是mysql数据库端口。 然后在一处下载文件的地方,看到了个可疑的url。 通过dnslog测试,发现是个ssrf漏洞。 尝试访问百度,得到出是完全回显的ssrf漏洞。 尝试这个ssrf是否支持其他协议,发现支持file协议,完全回显,又可以读文件,真舒服。 那么现在只需要让网站报错 爆出绝对路径,或者尝试去读取一些配置文件看看能否找到网站的绝对路径,最终读取到网站数据库的配置文件,那么就可以连接上数据库就可以拿到管理员账号密码了。 读取到 /etc/httpd/conf/httpd.conf 这个文件,发现网站路径为 /var/www/html 。 于是准备尝试去读取index.php发现居然没有内容,最后各种测试,各种组合,都没任何关于网站的回显,自闭了。 没办法,那就只有想办法让网站报错,看看路径对不对。 终于找到了个点让网站报错,发现之前的路径不对。 最终经过翻代码,找到了数据库配置文件,成功的找到了数据库账号密码。 成功连上了数据库。 最终成功进了后台。 后台还有个这个功能…… 嗯…… 非常好 over…… Uploading Attachment...
-
-
MFSA2024-07 Thunderbird: Security Vulnerabilities fixed in Thunderbird 115.8 (CVE-2024-1549) Severity 4 CVSS (AV:L/AC:M/Au:N/C:P/I:P/A:P) Published 02/20/2024 Created 02/22/2024 Added 02/21/2024 Modified 02/22/2024 Description If a website set a large custom cursor, portions of the cursor could have overlapped with the permission dialog, potentially resulting in user confusion and unexpected granted permissions. This vulnerability affects Firefox < 123, Firefox ESR < 115.8, and Thunderbird < 115.8. Solution(s) mozilla-thunderbird-upgrade-115_8 References https://attackerkb.com/topics/cve-2024-1549 CVE - 2024-15…
-
Red Hat: CVE-2024-36472: gnome-shell: code execution in portal helper (Multiple Advisories) Severity 7 CVSS (AV:A/AC:H/Au:N/C:C/I:C/A:C) Published 05/28/2024 Created 09/14/2024 Added 09/13/2024 Modified 11/27/2024 Description In GNOME Shell through 45.7, a portal helper can be launched automatically (without user confirmation) based on network responses provided by an adversary (e.g., an adversary who controls the local Wi-Fi network), and subsequently loads untrusted JavaScript code, which may lead to resource consumption or other impacts depending on the JavaScript code's behavior. Solution(s) redhat-upgrade-gnome-classic-session …
-
进行渗透测试之前, 最重要的一步就是信息收集,在这个阶段,我们要尽可能地收集目标组织的信息。所谓“知己知彼,百战不殆,我们越是了解测试目标,测试的工作就越容易。在信息收集中,最主要的就是收集服务器的配置信息和网站的敏感信息,其中包括域名及子域名信息、目标网站系统、CMS指纹、目标网站真实IP、开放的端口等。换句话说,只要是与目标网站相关的信息,我们都应该去尽量搜集。 【黑客仓库原创文章,写这么久不易,转载希望能带原创地址。】 1 . 1 收集域名信息知道目标的域名之后,我们要做的第一件事就是获取域名的注册信息,包括该域名的DNS服务器信息和注册人的联系信息等。域名信息收集的常用方法有以下这几种。 1.1.1 Whois 查询Who is是一个标准的互联网协议, 可用于收集网络注册信息,注册的域名、IP地址等信息。简单来说, Whois就是一个用于查询域名是否己被注册以及注册域名的详细信息的数据库(如域名所有人、域名注册商〉。在Whois查询中,得到注册人的姓名和邮箱信息通常对测试个人站点非常有用,因为我们可以通过搜索引擎和社交网络挖掘出域名所有人的很多信息。对中小站点而言,域名所有人往往就是管理员。在Kali系统中, Whois 己经默认安装,只需输入要查询的域名即可。 我们以www.xxx.com为教程演示;使用kali进行whois查询命令: JavaScript: Whois www.xxx.com这是一种比较古老的方法,但是现在,我们正常是使用国内比较大的资产搜索引擎进行收集。 举例(点击直接访问,或者在浏览器新建页面输…
-
在内网渗透中,当攻击者获取到内网某台机器的控制权后,会以被攻陷的主机为跳板,通过收集域内凭证等各种方法,访问域内其他机器,进一步扩大资产范围。通过此类手段,攻击者最终可能获得域控制器的访问权限,甚至完全控制基于Windows操作系统的整个内网环境,控制域环境下的全部机器。 横向移动中的文件传输通过文件共享-IPC执行net share命令,可以获得Windows默认开启的网络共享,其中C$为C盘共享,ADMIN$为系统目录共享,还有一个IPC$共享。 IPC(Internet Process Connection)是共享”命令管道”的资源,为了让进程间通信而开放的命令管道,通过提供可信任的用户名和口令,连接双方可以建立安全的通道并以此通道进行加密数据的交换,从而实现对远程计算机的访问。 实战中往往会建立IPC$连接,因为通过IPC$连接,不仅可以进行所有文件共享操作,还可以实现其他远程管理操作,如列出远程主机进程、在远程主机上创建计划任务或服务等。 建立IPC$连接需要具备以下两个条件: ①远程主机开启了IPC连接 ②远程主机的139端口和445端口开放 # IPC$ 连接 net use \\192.168.1.131\ipc$ # 建立空连接 net use \\192.168.1.131\ipc$ "password" /user:"Administrator" # 建立非空连接 # IPC$ 使用 net use # 查看本…
-
-
OS X update for ImageIO (CVE-2023-42932) Severity 5 CVSS (AV:L/AC:M/Au:N/C:C/I:N/A:N) Published 12/12/2023 Created 10/14/2024 Added 10/14/2024 Modified 01/28/2025 Description Deprecated Solution(s)
-
Ubuntu: (Multiple Advisories) (CVE-2024-35833): Linux kernel vulnerabilities Severity 4 CVSS (AV:L/AC:M/Au:N/C:P/I:P/A:P) Published 05/17/2024 Created 07/15/2024 Added 07/15/2024 Modified 08/06/2024 Description In the Linux kernel, the following vulnerability has been resolved: dmaengine: fsl-qdma: Fix a memory leak related to the queue command DMA This dma_alloc_coherent() is undone neither in the remove function, nor in the error handling path of fsl_qdma_probe(). Switch to the managed version to fix both issues. Solution(s) ubuntu-upgrade-linux-image-6-5-0-1017-starfive ubuntu-upgrade-linux-image-6-5-0-1020-raspi ubuntu-upgrad…
-
一、青龙组WEB web1 开局随便随便输入都可以登录,登上去以后生成了一个token和一个session,一个是jwt一个是flask框架的 这边先伪造jwt,是国外的原题 CTFtime.org / DownUnderCTF 2021 (线上) / JWT / Writeup 先生成两个token,然后利用rsa_sign2n工具来生成公钥 python3 jwt_forgery.py eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFhYWFhIn0.EnToBP4kzW6jbUqkC7fjt-FcCq9mOMhKWRqKpo12BsG464YTX2QNiBLuzgqJhnDlGF2Ukqb6oWXhFm0qiKrbg1skUb0FO2kMBkEvRLpyGJ7tXOzcndGDl-egaMa-mSN321RNW-aiCKJsij5Tf0HzQgBU8UCg1Zd8uJaybcj3oXOi eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImEifQ.IUanU3g_ZtyPjDnOJ9gockfRo1oOQLmQT0To_WYLi9I9PluHxbBId5d2wFiF-sIhGPuDtzPvShiE1ao0qnMlp3X7pVf-Qb-juaslvbnpR1rCKH2D3Kq4u1d2wEDvsgWVtjYA6s5NXrvJpzDcpZlzmx_6Ywn8caqVQ3kjlTv87OKO 得到public k…
-
Gentoo Linux: CVE-2023-51385: OpenSSH: Multiple Vulnerabilities Severity 6 CVSS (AV:N/AC:L/Au:N/C:P/I:P/A:N) Published 12/18/2023 Created 12/29/2023 Added 12/28/2023 Modified 01/28/2025 Description In ssh in OpenSSH before 9.6, OS command injection might occur if a user name or host name has shell metacharacters, and this name is referenced by an expansion token in certain situations. For example, an untrusted Git repository can have a submodule with shell metacharacters in a user name or host name. Solution(s) gentoo-linux-upgrade-net-misc-openssh References https://attackerkb.com/topics/cve-2023-51385 CVE - 2023-51385…
-
Ubuntu: (CVE-2023-52800): linux vulnerability Severity 4 CVSS (AV:L/AC:M/Au:N/C:P/I:P/A:P) Published 05/21/2024 Created 11/21/2024 Added 11/19/2024 Modified 02/11/2025 Description In the Linux kernel, the following vulnerability has been resolved: wifi: ath11k: fix htt pktlog locking The ath11k active pdevs are protected by RCU but the htt pktlog handling code calling ath11k_mac_get_ar_by_pdev_id() was not marked as a read-side critical section. Mark the code in question as an RCU read-side critical section to avoid any potential use-after-free issues. Compile tested only. Solution(s) ubuntu-upgrade-linux ubuntu-upgrade-linux-aw…
-
域内日志一般以.evtx结尾,因此我们需要搜索域内日志可以使用dir指令 dir/s/b *.evtx /s:表示递归搜索,包括子目录。 /b:表示以简洁模式显示结果,只显示文件路径而不包括其他信息。 这里我们可以直接使用logparser工具导出域内的日志信息。(在域控主机中) logparser工具采用的是SQL查询的方式进行过滤。 使用下面的指令可以通过strings列和eventid列过滤出域内用户的登录行为。 LogParser.exe -i:evt -o:csv "SELECT RecordNumber,TimeWritten,EventID,Strings,Message into C:\log5.csv FROM Security where EventID='4624' and Strings LIKE '%|Kerberos|%|%.%.%.%|%' and Strings not LIKE '%|%$|%'" -i:输入文件类型 -o:输出文件类型 在正常的域渗透过程中,我们直接拿到域控,并且在域控的主机上进行操作导出日志一般的不现实的,一般采用下面的三种方式导出域控的日志或者是指定成员主机的日志进行分析: 1.VPN的方式; 2.通过搭建socks隧道的方式; 3.通过远程木马的方式; 通过VPN的方式查询日志一般来说,通过VPN连接目标主机,进入内网环境进行操作。 这里我们假定已经获得域管理的账号,通过域管理凭据进行导出日志分析。 1.查询主机的登录记录首先获得域控的日志存储位置 dir /s/b \\10.10…
-
Alma Linux: CVE-2023-47038: Moderate: perl:5.32 security update (Multiple Advisories) Severity 7 CVSS (AV:L/AC:L/Au:S/C:C/I:C/A:C) Published 12/18/2023 Created 05/08/2024 Added 05/08/2024 Modified 01/28/2025 Description A vulnerability was found in perl 5.30.0 through 5.38.0. This issue occurs when a crafted regular expression is compiled by perl, which can allow an attacker controlled byte buffer overflow in a heap allocated buffer. Solution(s) alma-upgrade-perl alma-upgrade-perl-algorithm-diff alma-upgrade-perl-archive-tar alma-upgrade-perl-archive-zip alma-upgrade-perl-attribute-handlers alma-upgrade-perl-autodie alma-upgrade-per…
-
Amazon Linux 2023: CVE-2024-23325: Important priority package update for ecs-service-connect-agent Severity 8 CVSS (AV:N/AC:L/Au:N/C:N/I:N/A:C) Published 02/09/2024 Created 02/14/2025 Added 02/14/2025 Modified 02/14/2025 Description Envoy is a high-performance edge/middle/service proxy. Envoy crashes in Proxy protocol when using an address type that isn’t supported by the OS. Envoy is susceptible to crashing on a host with IPv6 disabled and a listener config with proxy protocol enabled when it receives a request where the client presents its IPv6 address.It is valid for a client to present its IPv6 address to a target server even though the whole ch…
-
滥用活动目录ACLs\ACEs权限https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/acl-persistence-abuse https://www.cnblogs.com/nice0e3/p/15879624.html DACL和ACE是与访问控制相关的概念,常用于操作系统和网络环境中。以下是对它们的详细解释: DACL(Discretionary Access Control List):DACL是一种访问控制列表,用于确定谁可以访问特定对象(如文件、文件夹、注册表项等)。DACL是以访问控制条目(ACE)的形式组成的列表。ACE(Access Control Entry):ACE是DACL中的基本单元,用于授予或拒绝对对象的访问权限。每个ACE定义了一个安全主体(如用户、组、计算机等)以及该安全主体所具有的权限。在DACL中,每个ACE包含以下信息: 安全主体(SID):标识被授权或被拒绝访问权限的用户、组或计算机的唯一标识符。访问权限:表示特定操作或权限(如读取、写入、执行等)。访问掩码:指定了实际授予或拒绝的权限。辅助访问掩码:在某些情况下,用于指定其他条件或限制。当访问对象时,系统将根据DACL中的ACE进行验证。如果存在与用户身份匹配的ACE,并且该ACE授予了所请求的权限,访问将被允许。如果没有匹配的ACE,或者存在与用户身份匹配的ACE,但是该ACE拒绝了所请求的权限,访问将被拒绝。 域管理员的ACE如下 其中,我们关…
-
FreeBSD: (Multiple Advisories) (CVE-2024-9122): electron31 -- multiple vulnerabilities Severity 9 CVSS (AV:N/AC:M/Au:N/C:C/I:C/A:C) Published 09/25/2024 Created 10/03/2024 Added 10/02/2024 Modified 01/28/2025 Description Type Confusion in V8 in Google Chrome prior to 129.0.6668.70 allowed a remote attacker to perform out of bounds memory access via a crafted HTML page. (Chromium security severity: High) Solution(s) freebsd-upgrade-package-chromium freebsd-upgrade-package-electron31 freebsd-upgrade-package-qt6-webengine freebsd-upgrade-package-ungoogled-chromium References CVE-2024-9122
-
SUSE: CVE-2024-36944: SUSE Linux Security Advisory Severity 4 CVSS (AV:L/AC:M/Au:N/C:P/I:P/A:P) Published 05/30/2024 Created 06/14/2024 Added 06/13/2024 Modified 08/28/2024 Description In the Linux kernel, the following vulnerability has been resolved: Reapply "drm/qxl: simplify qxl_fence_wait" This reverts commit 07ed11afb68d94eadd4ffc082b97c2331307c5ea. Stephen Rostedt reports: "I went to run my tests on my VMs and the tests hung on boot up. Unfortunately, the most I ever got out was: [ 93.607888] Testing event system initcall: OK [ 93.667730] Running tests on all trace events: [ 93.669757] Testing all events: OK [ 95.631064] ------------[ …